The Phylax Credible Layer Whitepaper
Despite DeFi's tremendous growth, security remains its Achilles' heel. Current approaches like audits, bug bounties, and automated monitoring have proven insufficient against sophisticated attackers. Even when vulnerabilities are discovered, the race between whitehats and blackhats often ends in costly exploits.
We recently announced the Credible Layer Whitepaper, and in this blog post, we will provide a quick overview of some of its key points. Not everyone has the time to read +50 pages afterall.
The Problem with Current Security Approaches
Current security solutions face several critical limitations:
- Frontrunning Protection: While tools like Phalcon can frontrun malicious transactions, attackers can bypass them using private mempools or by setting up their own validators.
- Next-block Mitigation: Strategies to pause protocols after detecting exploits assume attacks span multiple blocks - an assumption that's becoming increasingly unreliable.
- Heuristic Analysis: While automated tools can detect known vulnerability patterns, they generate too many false positives for real-time prevention and miss novel attack vectors.
We need a new approach that guarantees deterministic security without relying on probabilistic detection or reaction speeds.
Enter the Credible Layer
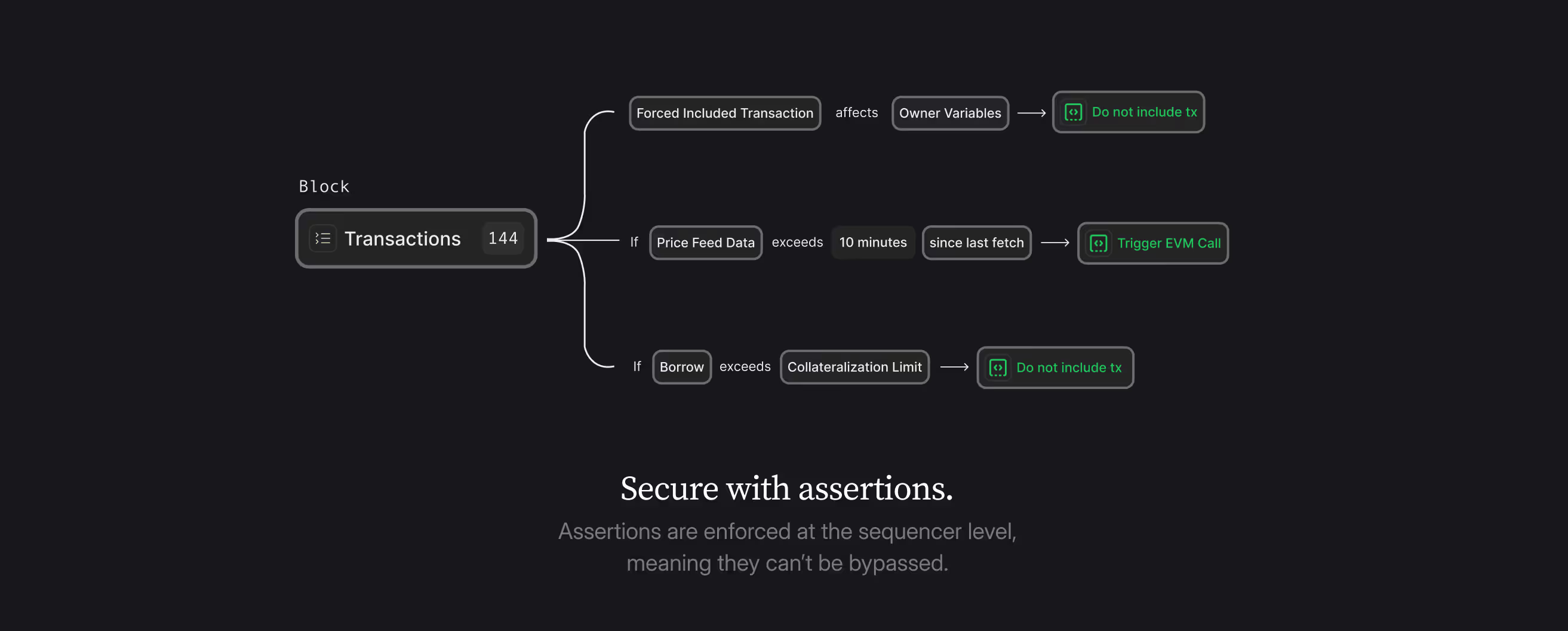
The Credible Layer introduces a novel security primitive: Assertions. Instead of trying to enumerate and protect against all possible attack vectors, protocols define what states should never occur.
Assertions: The Core Primitive
An assertion is a function that maps blockchain state to a boolean value:
Assertion: State → {true, false}
For example, assertions could specify that:
- Critical protocol parameters (owner addresses, implementation contracts) should never change
- Market prices shouldn't move more than X% in Y blocks
- More than Z% of lending positions shouldn't become underwater within N blocks
- Flash loans shouldn't be present in transaction traces
These assertions are executed off-chain in a modified EVM (PhEVM), allowing for complex checks that would be impractical or impossible to perform on-chain.
Assertions as Intents
While the blockchain space has recently embraced intents as a way to express desired outcomes, assertions can be viewed as their inverse - a sort of “negative intent" that specifies states that must never occur. This shift from prescriptive to proscriptive specification offers a powerful security abstraction. Rather than trying to enumerate all valid states or anticipate every possible attack vector, developers can declaratively define what constitutes an invalid state for their protocol. This approach is particularly powerful for security implementations, as it protects against both known and unknown vulnerabilities.
Whether an attacker exploits a code vulnerability, compromised private keys, or even compiler-level bugs, a well-crafted assertion can prevent the system from entering an invalid state. By focusing on what must not happen rather than exhaustively defining what can happen, assertions provide a more flexible and comprehensive security model that naturally scales with protocol complexity.
Flexible Security Without Redeployment
A crucial advantage of the Credible Layer's design is that assertions exist outside the protocol’s smart contract code. Unlike traditional security measures that require contract modifications and redeployment, assertions can be added or removed without touching the underlying protocol contracts. They simply point to the contract themselves to tell the base layer which contract to apply which rules to. This separation provides flexibility in managing protocol security. Teams can react to newly discovered attack vectors by deploying new assertions immediately, without the risks and coordination challenges of contract upgrades. Similarly, if an assertion proves too restrictive or unuseful, it can be quickly removed without affecting protocol operations. By decoupling security rules from protocol contract code, protocols can maintain robust, adaptable security without sacrificing immutable contracts' stability and reliability benefits.
The Mechanism: How It Works
The Credible Layer involves four key participants:
- Assertion Adopters (Protocols):
- Define assertions for their contracts
- Deposit funds for security fees and bounties
- Can specify automated mitigation actions (e.g., pause functions)
- Assertion Enforcers (Block Builders/Sequencers):
- Stake funds as a security bond
- Validate transactions against assertions before inclusion
- Earn fees for protecting protocols
- Get slashed if they allow invalid transactions
- Assertion Submitters (Security Researchers):
- Develop and propose assertions
- Earn rewards when protocols adopt their assertions
- Assertion Consumers (Whitehat and Blackhat Hackers):
- Submit two types of proofs:
- Proof of Possibility (PoP): Demonstrates potential vulnerability
- Proof of Realization (PoR): Proves hack has occurred
- Earn bounties for PoPs without needing to race attackers
- Submit two types of proofs:
The Security Model
The system's security relies on both economic and social incentives:
- Economic Incentives:
- Assertion Enforcers stake substantial bonds
- Protocols pay ongoing security fees
- Bounties reward the discovery of vulnerabilities
- Slashing punishes enforcement failures
- Social Slashing:
- Any collusion is cryptographically provable
- Legal ramifications for facilitating attacks
- Permanent reputation damage
- Future opportunity cost in the crypto ecosystem
While an attacker might theoretically offer bribes exceeding the staked bonds, the combination of economic penalties and social consequences creates a powerful deterrent. Additionally, all the entities we work with are already trusted to select and order which blocks are included. In other words, we are not giving them any more power to enable hacks than they already have.
Technical Implementation: Ajax
Our first implementation, Ajax, is designed for OP Stack-based rollups and comprised of several key components:
- PhEVM: Modified EVM interpreter for executing assertions
- Access to pre- and post-transaction states
- Custom precompiles for efficient state access
- Parallel assertion execution
- OP-Talos: Middleware for block builders
- Integrates with Builder API
- Validates transactions against assertions
- Manages proof submission and slashing
- Smart Contracts:
- State Oracle: Manages assertions and proofs
- Assertion Registry: Tracks enforcers and security deposits
- Mitigation Execution: Handles automated responses
Beyond Single Sequencer Networks
The system is designed to eventually work in both centralized and decentralized environments as our goal is to protect capital and users wherever they may be:
Multi-Builder Networks (e.g., Ethereum)
The Credible Layer's architecture extends to decentralized environments with multiple block builders, such as the Ethereum mainnet. The system maintains a registry of "Credible Builders" - block builders who have enrolled as Assertion Enforcers and are committed to enforcing protocol assertions. Protocols can then implement checks that reject transactions from non-credible builders, effectively ensuring their security guarantees remain intact regardless of the network's builder landscape. This creates a natural competitive advantage for participating builders, who can attract protocol activity through their security guarantees while also earning security fees. The system even supports "Credible Bundles" for application-specific sequencing, allowing for fine-grained security enforcement at the transaction bundle level rather than entire blocks. This flexibility ensures the Credible Layer can adapt to various network architectures while maintaining its security properties.
Cross-Chain Future
The Credible Layer's vision extends beyond single-network security to support assertions spanning multiple networks, creating a unified security layer across L1s and L2s with standardized proof formats and verification. Cross-chain assertions are crucial as DeFi increasingly operates across multiple networks, where vulnerabilities in one network can cascade into others.
For instance, a bridge exploit on one chain could trigger assertions on connected networks, preventing the attacker from withdrawing or using the stolen funds across the ecosystem. This becomes particularly powerful for protocols operating across multiple chains, allowing them to define security invariants that span their entire system rather than treating each deployment in isolation.
Such cross-chain security guarantees are increasingly vital as protocols deploy across numerous L2s and bridges become critical infrastructure, making ecosystem-wide security coordination essential for preventing sophisticated attacks that exploit cross-chain interactions.
Financial Primitives
The Credible Layer enables several novel financial primitives that were previously impractical due to blockchain's inherent difficulty in quantifying risk and defining adverse events:
- Security Bond Markets
- Assertion Enforcers can issue bonds against future fee revenue
- Reduces capital requirements while maintaining security
- Creates yield opportunities for token holders
- Unlike traditional blockchain bonds, these are backed by mathematically verifiable future revenue streams tied to assertion execution
- Automated Insurance
- Traditional on-chain insurance has struggled due to the difficulty of defining what constitutes a "hack" and determining if one has occurred
- Assertions solve this fundamental problem by providing clear, programmatic definitions of invalid states
- Claims processing becomes deterministic - if an assertion is violated, the insurance pays out
- This removes the need for manual investigation, litigation, or governance votes that make current crypto insurance products inefficient
- Market-driven premium pricing becomes possible as risk can be quantified based on assertion characteristics
- Restaking Integration
- Validators can delegate staked ETH to Assertion Enforcers to earn additional yield
- These Assertion Enforcers (like major sequencers or block builders) earn consistent fees from protocols for security enforcement
- Validators can capture a portion of these fees by delegating their staked ETH to trusted Assertion Enforcers, earning returns beyond basic staking rewards
- This creates a two-sided market:some text
- Assertion Enforcers can operate with less upfront capital by "borrowing" security deposits from validators
- Validators can maximize yield on their staked ETH by selecting reliable Assertion Enforcers with strong security fee revenues
- The mechanism aligns incentives across the stack: validators are motivated to delegate to trustworthy Assertion Enforcers since their stake is at risk if the Enforcer allows a hack
- This effectively extends Ethereum's security model to the application layer, letting the same capital secure both consensus and application-level security
These primitives represent more than just financial products - they're tools that become possible when we can programmatically define and verify security conditions. By making security quantifiable and verifiable, the Credible Layer opens up an entirely new design space for DeFi primitives that previously couldn't exist due to the difficulty of expressing and verifying security assumptions on-chain.
The Road Ahead
While we're starting with hack prevention, the Credible Layer creates possibilities for new applications and paradigms:
- Counter-Factual Applications Rather than defining every valid state and interaction, protocols can be built by specifying what states must never occur. This inverted model offers powerful new abstractions - imagine a lending protocol that doesn't need to specify every valid interest rate calculation but instead asserts that user positions must remain solvent and arbitrage opportunities can't exceed certain thresholds. This approach could lead to more robust protocols that are easier to reason about and audit while being naturally resistant to edge-case exploits.
- Provable Off-Chain Computation The Credible Layer's assertion mechanism provides a framework for trustless state transitions that could revolutionize how we think about blockchain scalability. By moving complex computations off-chain while maintaining on-chain verifiability, we can build applications that were previously impractical due to gas costs. Imagine high-frequency trading systems or complex financial derivatives that operate primarily off-chain but retain blockchain-level security guarantees through assertions about their state transitions.
- Contract-Based Soft-Forking By enabling protocols to influence network consensus through assertions, we're introducing a new kind of blockchain governance. Protocols can effectively create "soft forks" by defining states that the network should reject without requiring node software updates. This could enable protocols to evolve their security models dynamically and allow communities to enforce standards or blacklist malicious behavior in a more decentralized way than current governance mechanisms allow.
We're actively working with L2 networks on initial implementations. Looking ahead, we're focused on:
- Decentralizing assertion data availability to remove single points of failure
- Enhancing capital efficiency through restaking and bond markets, making security more accessible to smaller protocols
- Supporting cross-chain assertions to secure the growing multi-chain ecosystem
- Expanding middleware support to all major rollup frameworks, making the Credible Layer a universal security standard
Join Us
The Credible Layer represents a fundamental shift in blockchain security. Instead of reacting to attacks, we're creating an environment where hacks are prevented by the underlying infrastructure.
If you have any questions about the Credible Layer or the whitepaper in general, please join our Discourse and join the discussion.
If you're interested in integrating the Credible Layer or contributing to its development, join our Telegram chat.
This is just the beginning. We envision the Credible Layer becoming as fundamental to DeFi as AMMs or lending protocols - a standard primitive that ensures the security of our rapidly evolving ecosystem.

.png)
.png)