How DeFi Actually Becomes Low-Risk: A Response to Vitalik
I’m sure you saw Low-risk defi can be for Ethereum what search was for Google, Vitalik’s most recent piece on how DeFi on Ethereum will win and bring value back to Ethereum.
Vitalik's vision is spot on: the future depends on low-risk DeFi rails. Institutions are already demanding exactly what he describes—stablecoin settlements, overcollateralized lending, and tokenized treasuries. Wall Street is ready (66% are already experimenting in DeFi), and the regulatory barriers that once seemed insurmountable are finally clearing.
But there's a critical gap between vision and reality. "Low-risk" in design doesn't mean "low-risk" in operation.
The Problem with "Low-Risk" as a Product Category
Nearly 50% of hacked protocols in the last 5 years had passed audits.
Take Euler Finance—the poster child for institutional-grade DeFi. Fully collateralized lending, audited 10 times by six reputable firms, battle-tested across market cycles. Then it lost $196 million in a single transaction.
The Systemic Risk Reality
Even "safe" primitives become unsafe when composed. The DeFi stack creates emergent risks that no individual audit can anticipate. History proves that:
- Oracle manipulation across multiple protocols
- Governance attacks that exploit cross-protocol dependencies
- Flash loan attacks that exploit composability itself
- Economic exploits that bypass all code-level security
The limiting factor for institutional adoption isn't regulation—it's security. And what makes DeFi safe isn't the product, it's the safety infrastructure around it.
What Credible Low-Risk DeFi Actually Requires
If we want trillions flowing into the rails Vitalik describes, we need more than good design:
This requires flipping the script on security a bit: Audits hunt for every possible technical bug. Monitoring systems track every anomaly, but no prevention. Bug bounties reward finding theoretical vulnerabilities. And here's the uncomfortable truth: nobody actually cares about "broken code," they care about the monetary consequencrs of broken code.
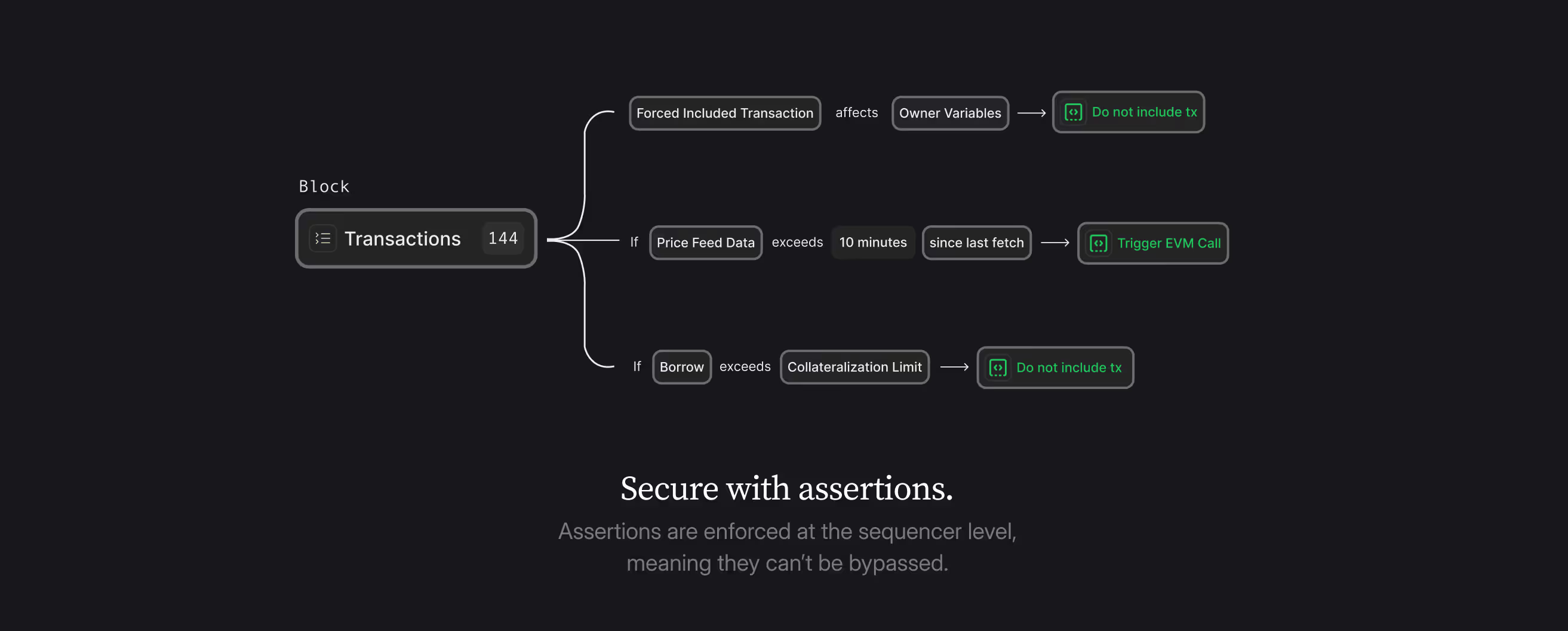
We need real-time prevention infrastructure that defines and catches attacks before they drain funds. A focus on the funds lost, rather than the million technical paths that led to those funds being lost, is advantageous from a design perspective. Low-risk, after all, speaks to the financial risk of allocating capital, and it is that risk that needs direct attention.
The Security Layer
Vitalik is absolutely right about the destination. But the journey requires acknowledging that security is infrastructure, not a product feature.
The protocols he envisions—stable, reliable, and institution-ready—don't emerge naturally through battle testing. They emerge through deliberate investment in safety systems that operate continuously, transparently, and independently.
We're building that infrastructure.

.png)
.png)