Network-Native Security: Why DeFi Needs Hack Prevention Built Into the Blockchain Itself
Moving beyond external monitoring to security that inherits the same guarantees as the network.
The current approach to DeFi security follows a familiar pattern: build your protocol, deploy it, then hope external services catch problems before they become exploits. This model—borrowed from traditional web applications—fundamentally misunderstands what makes blockchain different from centralized systems.
When we bolt external security onto blockchain infrastructure, we're undermining the very properties that attracted us to blockchain in the first place.
The Architecture Problem
Consider how current DeFi security actually works:
The service sits outside the network, watching transactions after they've been submitted, racing against attackers to respond quickly enough to minimize damage. This creates multiple failure points:
- External API calls that can fail
- Third-party services that can go offline
- Additional trust assumptions beyond the network itself
- Race conditions between detection and response
- A tradeoff between latency and security for your app and security
Network-native approach: Your protocol → Network validates your rules → Invalid transactions rejected
The key difference: network-native security uses the same infrastructure that validates transactions. Same validators, same consensus mechanism, same availability guarantees.
This architectural shift eliminates the failure points that plague external security solutions. Rules are enforced with the same consistency as every other action the chain takes, using the infrastructure that's already proven to handle billions in value.
Let’s break it down.
The Trust Assumption Problem
Every external security service introduces new trust assumptions. When you add monitoring, alerting, or AI-based detection, you're asking users to trust not just your protocol and the underlying blockchain, but also:
- The security vendor's algorithms and decision-making
- Their uptime and operational reliability
- Their ability to respond faster than attackers can hack
- Their resistance to compromise or manipulation
For institutions, especially, each additional trust assumption creates compliance and risk questions. Risk teams must evaluate not just the protocol they're allocating to, but every service provider in that app’s security stack.
Network-native security eliminates this proliferation of trust assumptions. If users trust the network to process their transactions, they should also trust it to enforce security rules. The same consensus mechanism that prevents double-spending also prevents rule violations.
The Regulatory Clarity Problem
Regulatory frameworks increasingly distinguish between truly decentralized systems and those that merely appear decentralized. The CLARITY Act, for example, requires that mature blockchain systems not be "controlled by any person or group under common control."
The Presidential Working Group on Digital Assets recommends builders “consider emergency stops and circuit breakers for unexpected smart contract issues.” Read more on that here.
External security providers create exactly the kind of centralized control points that could disqualify systems from regulatory protection. When an AI security system can unilaterally block transactions or a monitoring service can change detection parameters, who really controls the protocol?
Maybe they say they won’t, but if they can, and you assume they won’t, that’s just trust.
Trustless, remember?
Network-native security also preserves decentralization by maintaining the same governance model for security rules as for protocol upgrades. Rules can be defined through existing governance channels and enforced by existing consensus mechanisms. No new control points, no additional centralization.
The Performance Problem
External security solutions inevitably introduce latency and throughput constraints. Every transaction must be:
- Submitted to the network
- Analyzed by external systems
- Either allowed to proceed or flagged for intervention
This multi-step process creates bottlenecks and race conditions. In many cases, the delay between detection and response can mean the difference between preventing an exploit and watching it succeed.
Essentially, you find that this can be summarized as a latency-security tradeoff where either you slow your app down to run security checks or you forgo them and make the checks obsolete.
Network-native security validates rules in parallel with transaction execution. There's no additional latency because rule validation happens as part of the same process that validates transaction signatures and state transitions.
The Transparency Problem
External security solutions often operate as black boxes. AI systems make decisions based on opaque algorithms. Monitoring services flag transactions as "suspicious" without clear criteria. Users and institutions are asked to trust security measures they cannot verify or audit.
This opacity creates problems for:
- Developers who need to understand why transactions are being rejected
- Institutions whose compliance teams require transparent risk controls
- Users who want to verify the security measures protecting their funds
Network-native security rules are transparent by design. They exist as smart contracts that can be read, audited, and verified by anyone. Just like a dApp’s smart contracts.
The same transparency that makes DeFi protocols auditable extends to their security mechanisms now.
The False Choice Between Security and Decentralization
The current security landscape forces protocols to choose between protection and principles. Want better security? Accept additional trust assumptions and centralization points. Want to maintain decentralization? Accept higher risk and limited security options.
This is a false choice created by architectural limitations, not fundamental constraints. Network-native security proves that stronger protection (prevention)and better decentralization can work together.
By building security into the network layer itself, we can have:
- Deterministic enforcement without trusted intermediaries
- Transparent rules without sacrificing prevention
- Institutional-grade security without compromising decentralization
- Regulatory compliance without external control points
Real-World Implementation
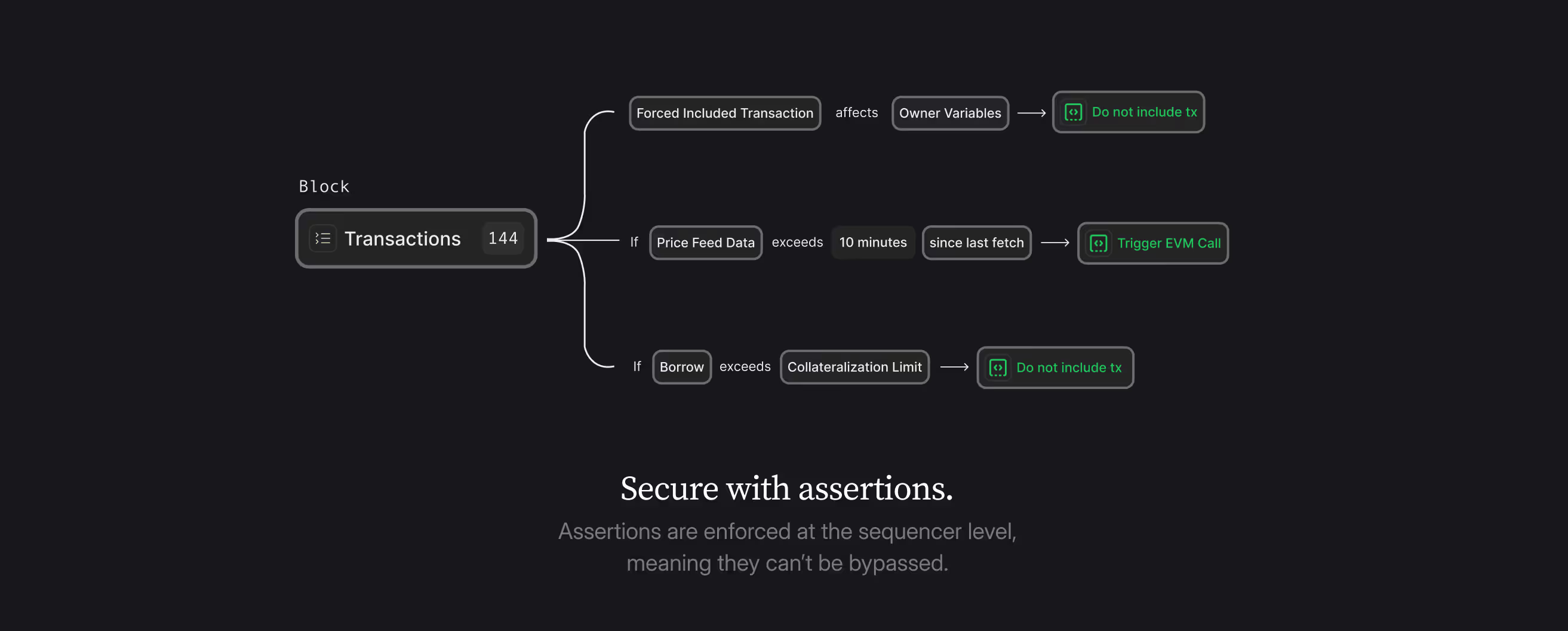
Network-native security isn't theoretical; it's being implemented today as the Credible Layer. Protocols define security rules called assertions, which are enforced by the network itself during transaction processing.
These rules can prevent:
- Unauthorized contract upgrades
- Market manipulation attacks
- Liquidity threshold violations
- Cross-protocol exploit vectors
All while maintaining the same trust assumptions as the underlying blockchain. Explore more use cases for assertions here.
The Path Forward
Current DeFi security relies on external monitoring services that operate separately from blockchain infrastructure. Despite widespread adoption, these approaches haven't prevented significant losses—$2 billion in exploits occurred already in 2025—while introducing additional trust assumptions that complicate regulatory compliance and institutional adoption.
Network-native security integrates prevention directly into consensus mechanisms. Rather than detecting problems after transactions are submitted, this approach validates security rules during transaction processing itself. Invalid transactions are rejected before execution, not flagged for post-hoc intervention.
The technical infrastructure for network-native security is operational today. Regulatory frameworks increasingly favor systems without external control points. Protocols evaluating long-term security architecture now have a clear alternative to external monitoring: security that operates with the same guarantees as the blockchain itself.

.png)
.png)