DATs Are Sidelined.
Institutional crypto holders manage tens of billions in digital assets, yet most operate with a fundamental inefficiency: they're leaving hundreds of millions in yield on the table through overly conservative buy-and-hold strategies.
This conservatism, while suboptimal from a pure return perspective, reflects entirely rational responses to the current security and regulatory landscape.
The Buy-and-Hold Trap
Corporate treasuries and institutional crypto vehicles have become large holders of digital assets, managing sophisticated portfolios worth tens of billions collectively. Yet despite this scale and sophistication, most employ surprisingly basic strategies.

Most corporate treasuries hold their crypto assets idle, earning zero yield on billions in holdings. Even when institutions pursue yield generation, they typically limit themselves to basic ETH staking rewards, earning 1-3% annually, a fraction of what's available through established DeFi protocols. In the case of MSTR, they are simply holding spot. Other lending strategies could generate 6-8% returns on the same underlying assets.
We're seeing early validation of this trend. Sharplink Gaming recently announced potential deployment of some of their $3.6B ETH holdings onto Linea to capture yield opportunities, signaling that institutional appetite for sophisticated DeFi strategies is real.

Security Concerns Drive Conservative Strategies
The reluctance to pursue higher yields isn't wrong; it comes from genuine security concerns that have shaped institutional crypto strategies. Corporate treasuries and institutional fund managers operate under strict fiduciary duties. Smart contract vulnerabilities have led to billions in losses each of the previous years, with DeFi protocols accounting for the majority of incidents. Perhaps more concerning for institutional investors, many of these breaches occurred in previously audited projects.
Historically, the unsteady regulatory environment has compounded these concerns. There is positive movement on that front, however, as the President's Working Group on Digital Asset Markets and the SEC are providing clearer guidelines for smart contract-based finance that will finally open the way for this capital to come on-chain. With that hurdle cleared, the decision for an institution to capture DeFi yield comes down to pure risk.
Traditional finance has created standardized risk frameworks that allow institutions to deploy capital efficiently across rated instruments. A pension fund can confidently purchase AA-rated corporate bonds, investment-grade municipal debt, or Treasury securities because decades of regulatory oversight, standardized accounting, and legal precedent have made these instruments predictable. Rating agencies, such as Moody's and S&P, provide consistent evaluation criteria, while regulatory frameworks ensure transparent reporting and provide legal recourse in the event of errors.
However, these same institutions cannot touch unrated startup debt, exotic derivatives without regulatory approval, or securities lacking proper disclosure documents, not because the underlying businesses are necessarily riskier (they usually are), but because the institutional infrastructure for evaluation and recovery simply doesn't exist.

DeFi protocols today occupy this same "unrated" category: potentially superior risk-adjusted returns, but lacking the standardized evaluation frameworks and legal certainty that fiduciary standards require.
The fundamental issue isn't that DATs lack appetite for yield or sophistication to evaluate DeFi protocols. Rather, current security infrastructure forces an impossible choice: accept unquantifiable smart contract risk, or build unsustainable compliance and analysis overhead across dozens of vendors and protocols. Without standardized frameworks that provide guarantees, even the most sophisticated DAT cannot justify the fiduciary risk of moving beyond basic holdings regardless of yield potential.
The current security infrastructure hasn't addressed institutional needs effectively. Traditional audit firms provide costly point-in-time security reviews, yet cannot guarantee ongoing protection as protocols evolve. Monitoring services from companies like Chainalysis detect suspicious activity but operate reactively, identifying problems after they occur rather than preventing them. Insurance coverage remains limited, with most DeFi protocols lacking institutional-grade protection.
These factors create a risk-return calculation that favors extreme conservatism. For a DAT, the downside risk of a smart contract exploit far outweighs the upside potential of additional yield.
Deterministic Security Changes the Equation
Institutions want blockchain's efficiency gains—24/7 settlement, programmable compliance, reduced intermediaries—but fear that hack losses become permanently finalized. The emergence of deterministic security infrastructure could resolve this risk-return dilemma by preventing invalid transactions from executing in the first place. This enforcement occurs at the network level without requiring trust in external parties, allowing institutions to capture blockchain efficiency while avoiding finality risk.
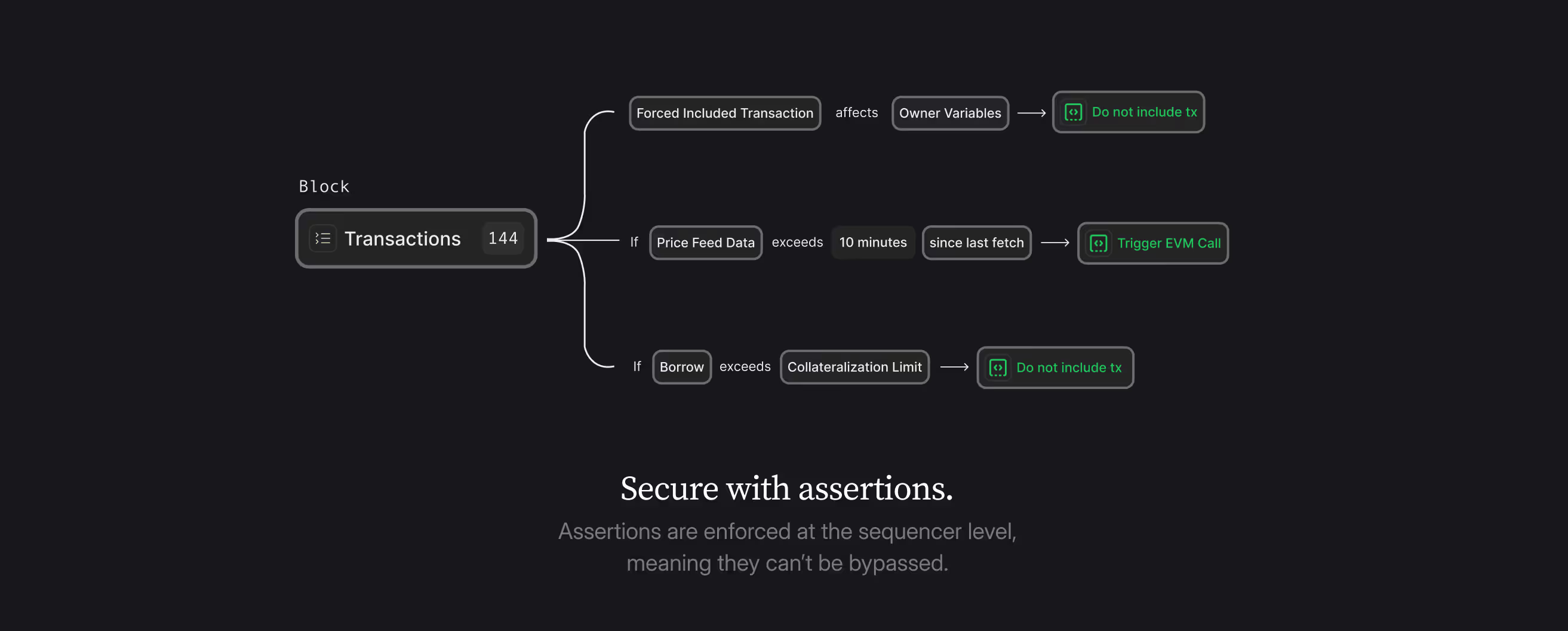
This approach works by enabling the dApps to define security rules, called assertions, that specify states the protocol must never enter. For example, an assertion might require that total assets always exceed total liabilities in a lending protocol, or that price movements cannot exceed specific thresholds within a given timeframe. A good example is global health checks that are run on every operation that changes the health factor of a position, but that is not allowed to put the position under water. If, for some reason, there’s a bug in the code and a hacker found a way to exploit it to put positions under water that shouldn’t be, then it will be caught by the assertion. These rules are then enforced at the network level during transaction processing by the network itself, making violation of each rule deterministically impossible rather than merely detectable.
The distinction matters enormously for institutional risk management. Current approaches require DATs rely on external monitoring services, audit reports, and insurance policies, all of which introduce counterparty risk and cannot guarantee prevention. Deterministic security eliminates these dependencies by making the network itself responsible for enforcement. If a transaction would violate a security assertion, it simply cannot execute, regardless of the attacker's sophistication or resources.

This architecture addresses the core institutional concerns that drive conservative strategies. Fiduciary duty requirements are satisfied because security violations become impossible rather than just monitored. Regulatory compliance is simplified because all security rules are publicly verifiable on-chain, providing transparent audit trails for regulators. Operational risk is reduced because institutions no longer depend on external security services or complex vendor relationships.
The implications for yield generation are huge.
DATs could confidently deploy capital into DeFi protocols protected by deterministic security, knowing that fundamental safety invariants cannot be violated. Rather than earning 1-3% through basic staking, institutional capital could access 4-10% yields through protected, battle-tested lending protocols like Aave while maintaining the absolute security guarantees fiduciary duty requires.
The Path Forward
The institutional crypto market stands at an inflection point. Regulatory clarity continues improving while DeFi infrastructure matures, yet the fundamental security concerns preventing capital deployment remain unresolved through current approaches. DATs managing tens of billions in assets continue operating suboptimally because existing security infrastructure cannot provide the guarantees a fiduciary duty requires.
Deterministic security offers a path forward that addresses institutional needs without compromising on yield potential. By making protocol violations as defined by the dApp impossible rather than detectable, this approach enables DATs to pursue sophisticated strategies while maintaining fiduciary responsibility.
For DATs currently leaving hundreds of millions in yield on the table, the question isn't whether to embrace more sophisticated strategies; it's whether to do so with security architecture designed for institutional requirements.

.png)
.png)