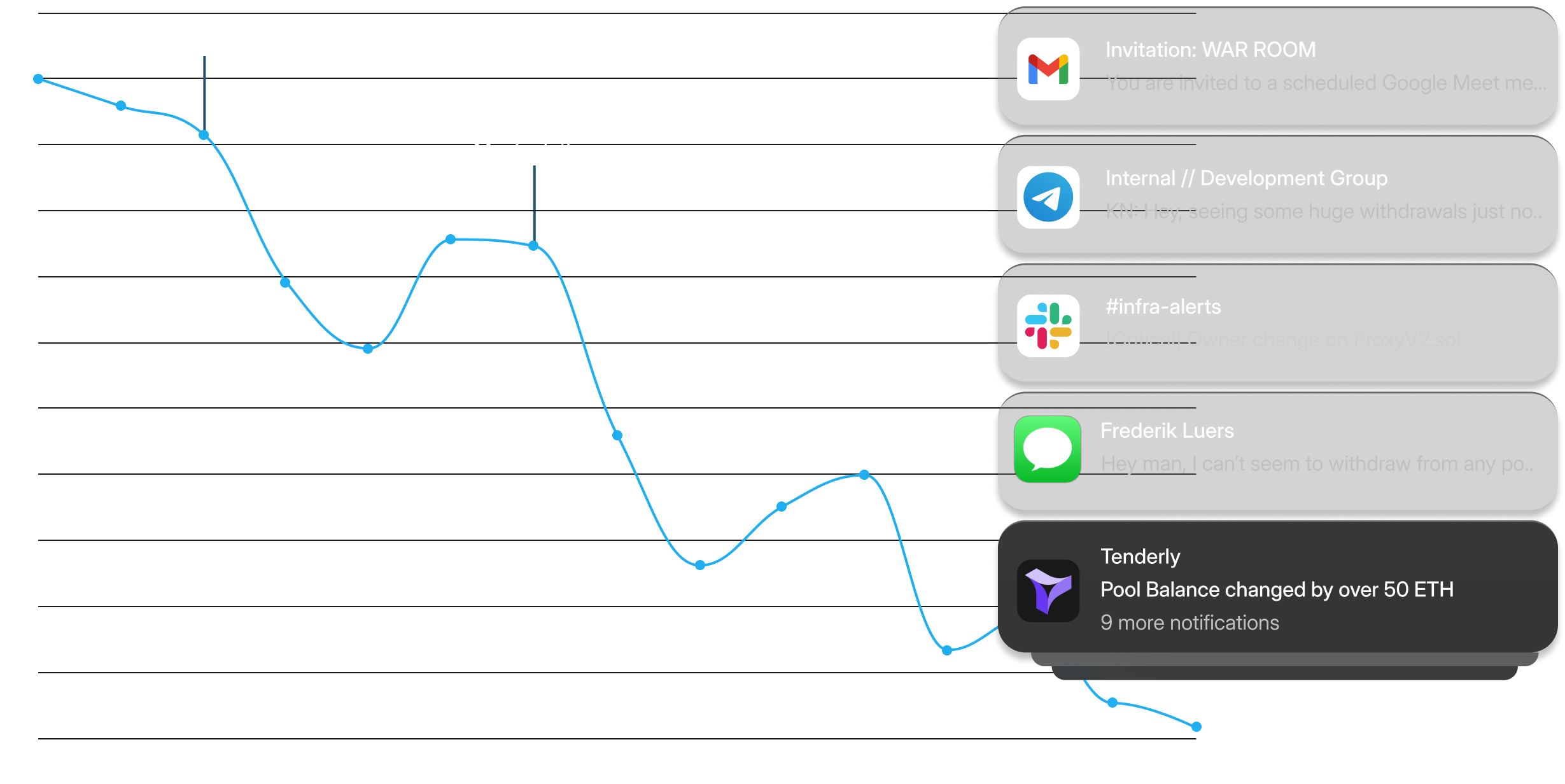
The worst day for your dApp looks like this:
How leading protocols are securing capital
$16M
Assets under protection
50+
Types of hacks covered
4 apps
Enforced by the block builder
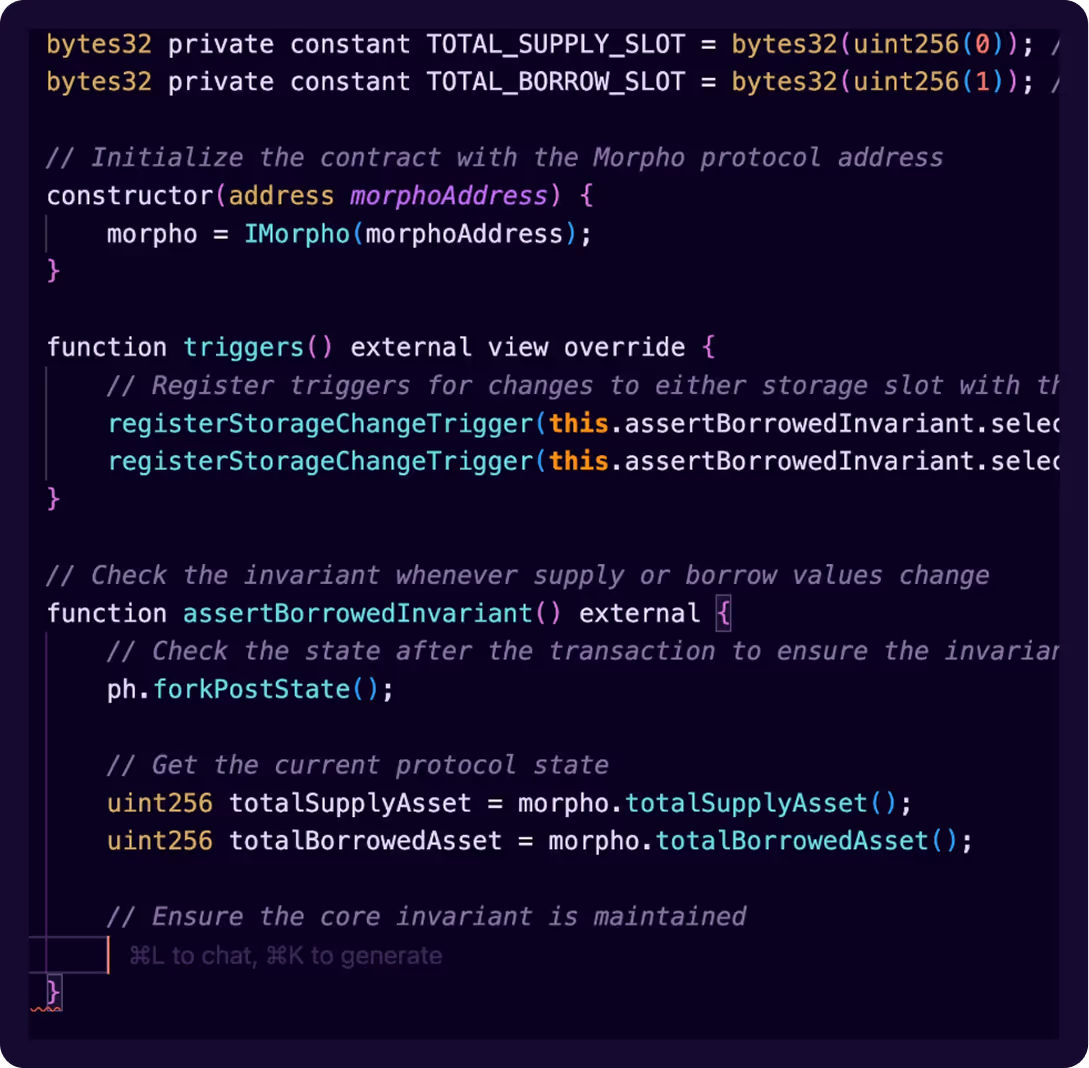
Setup assertions: verifiable and
enforced in real-time.
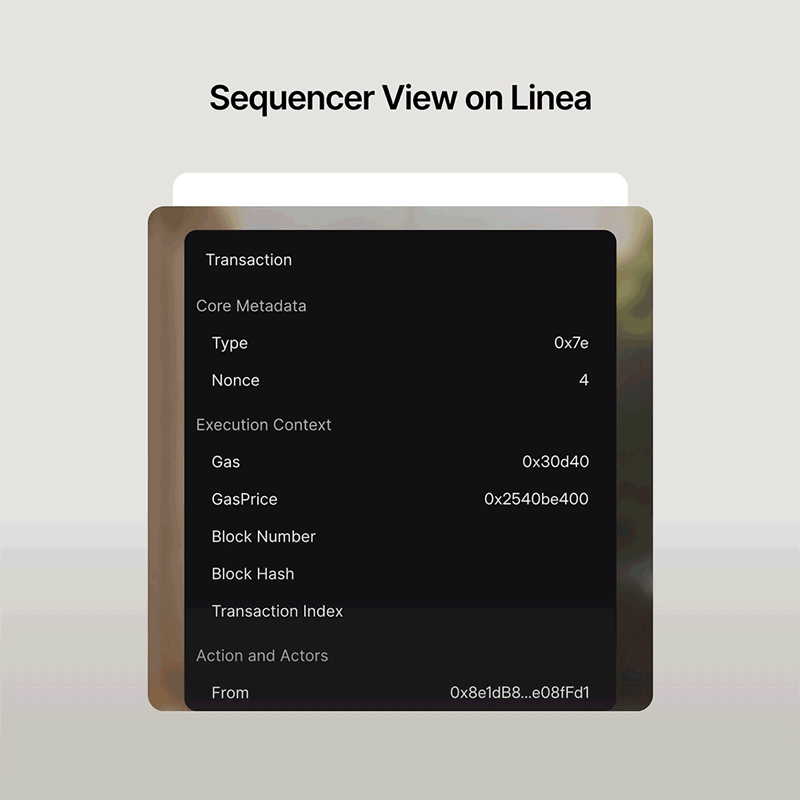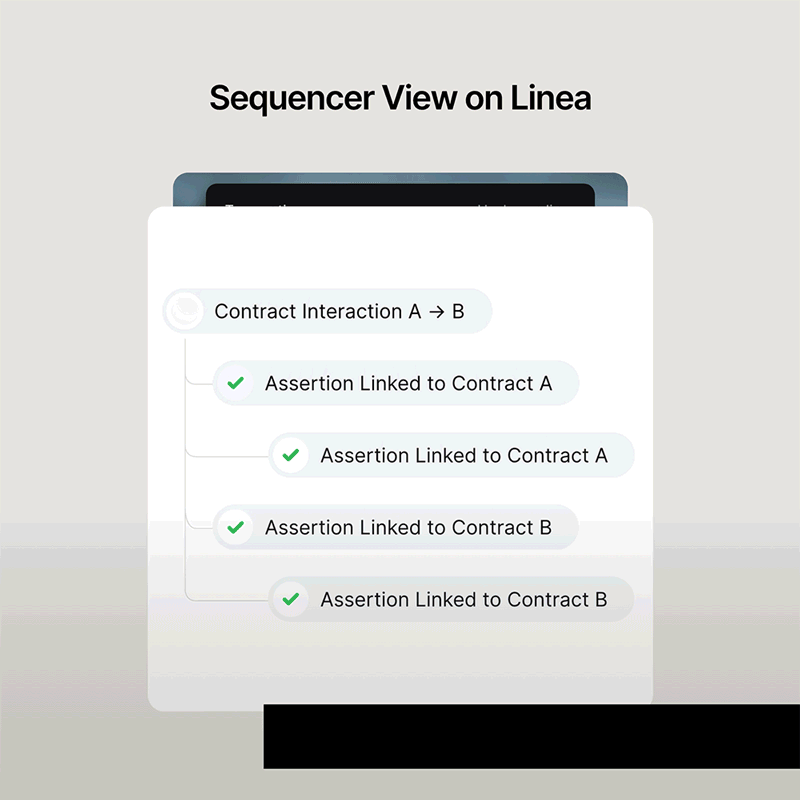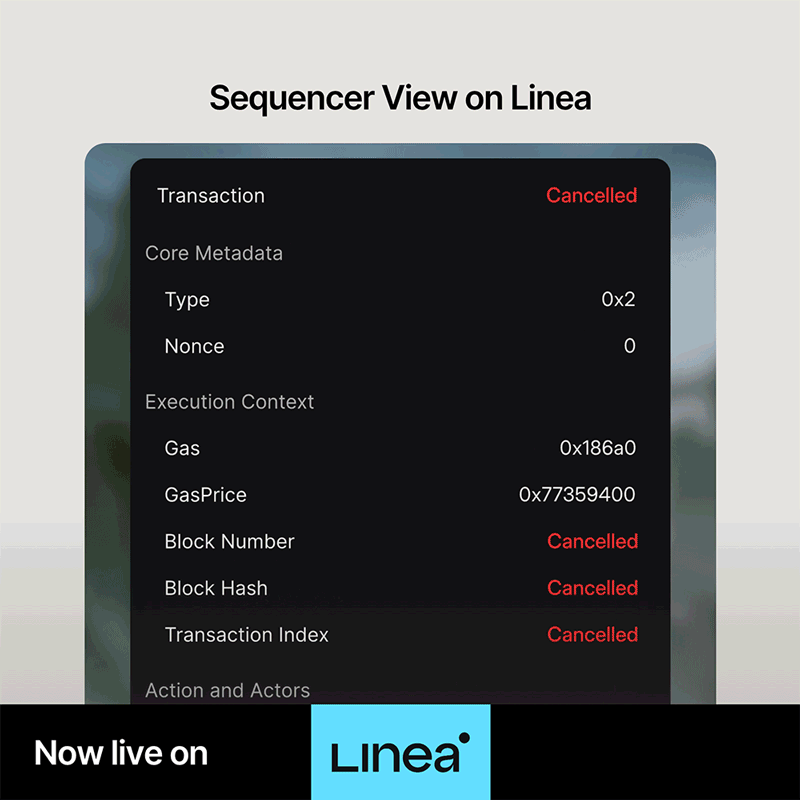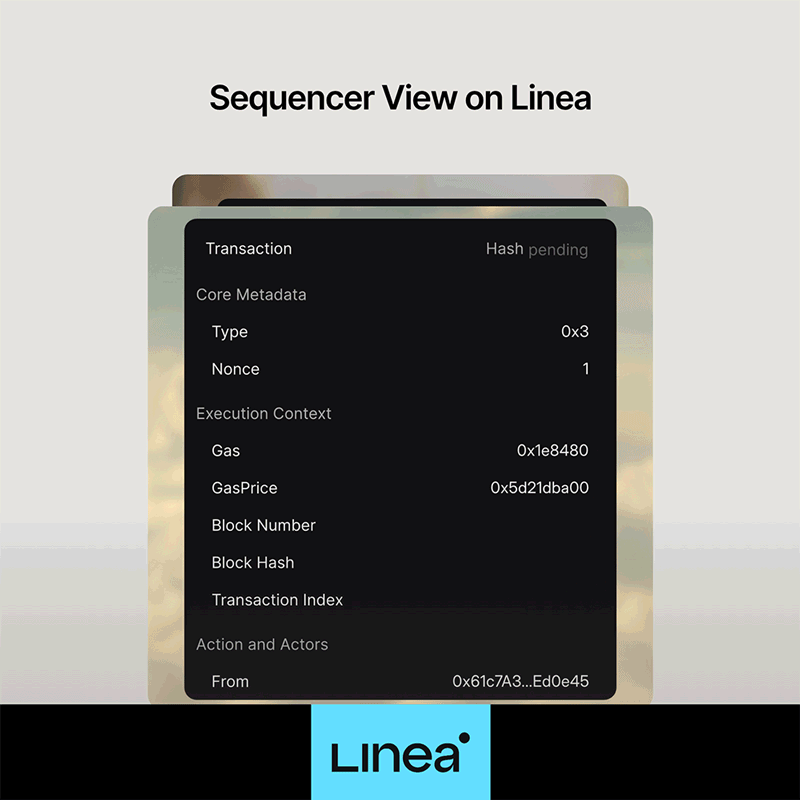
Product updates
¹Phylax states that:
We have not received any National Security Letters or FISA court orders. We have not been subject to any gag order by a FISA court. We have not received any warrants from any government organization. We have not placed any backdoors in our software. We have not received or complied with any government requests regarding our project. We have not altered our code or services at the request of any government agency.
If this statement is removed from future versions of this document, it is likely that Phylax has been served with a government subpoena and is unable to communicate this fact.
This statement will be updated on the 1st of every month.
Last updated: Feb 4 2026













