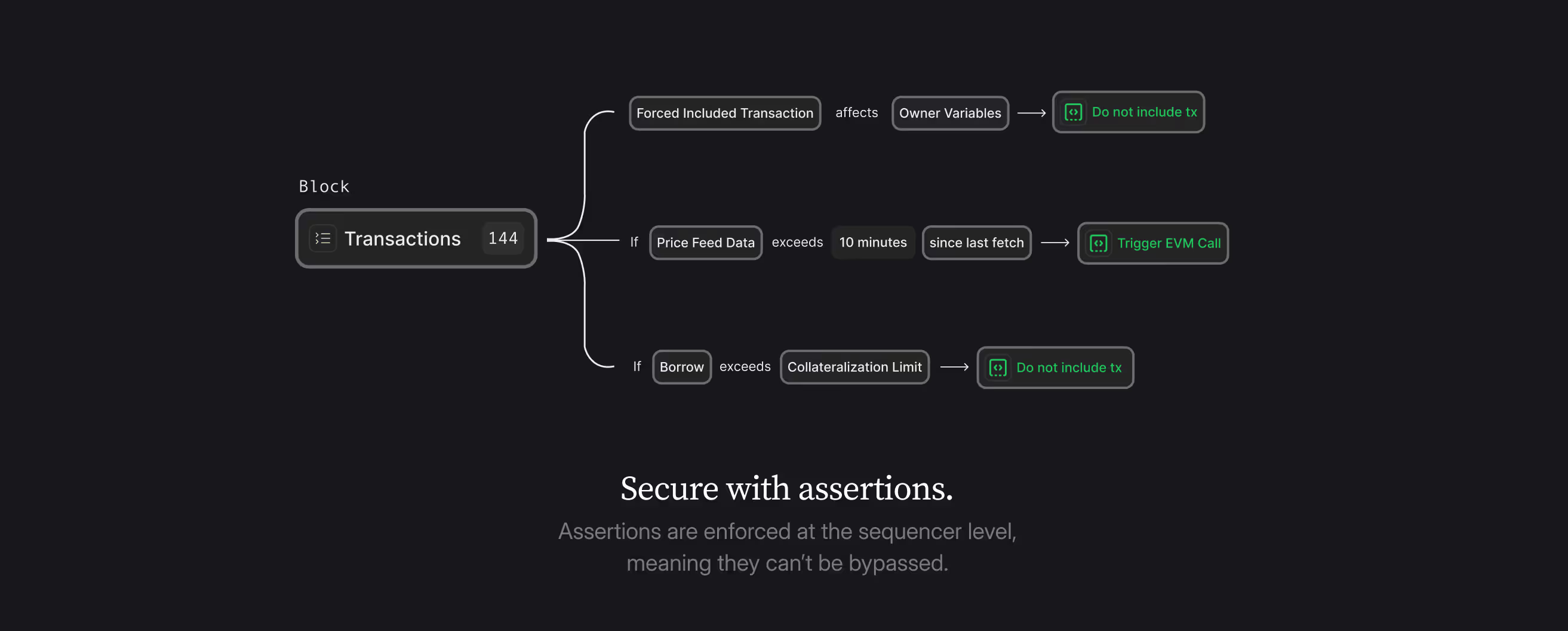
Blockchain security has historically been constrained by the limitations of the EVM execution environment. Smart contract developers have been forced to work within these boundaries, often leading to complex, inefficient solutions for preventing unwanted contract behavior. The Phylax Credible Layer introduces a novel approach to this problem through the use of cheatcodes, which drastically expands what is possible for on-chain assertions.
What Are Cheatcodes?
Cheatcodes in the Phylax Credible Layer are special instructions implemented in native code (compiled programming languages like Rust that execute directly on the machine) rather than EVM bytecode (which runs in the virtual machine). This implementation allows them to access system-level functionality and transaction data that standard EVM code cannot reach. While sometimes referred to as "precompiles" in other contexts, we use the term "cheatcodes" as it's more familiar and intuitive for developers coming from testing frameworks like Foundry and Hardhat.
These cheatcodes provide a powerful interface between assertion contracts and the underlying Phylax environment, enabling developers to:
- Inspect any contract's storage directly at the EVM level, reading private variables and protected state without needing accessor functions or permissions
- Create and switch between VM snapshots to compare values before and after specific operations, simulating "time travel" within transactions
- Access dynamic transaction execution data, including the complete call stack, function parameter values, and all emitted events in real-time
Why Cheatcodes Are Game-Changing
The power of Phylax cheatcodes lies in their ability to transcend normal EVM limitations. Traditional smart contracts operate within a tightly controlled sandbox where visibility into transaction context, call data, and state changes is severely restricted. Cheatcodes break through these barriers as they aren’t part of the EVM and operate above it.
Breaking Down Barriers
With Phylax cheatcodes, developers can:
- Access storage slots directly, even if they're private variables
- Observe all state changes within a transaction, including intermediate values
- Inspect call data across an entire transaction
- Switch between pre/post-transaction states seamlessly
- Capture and analyze log emissions
This level of visibility was previously impossible with standard Solidity and opens up entirely new paradigms for contract security and exploit prevention.
The Trigger System: Decide When Your Assertions Execute
A key component of the Phylax Credible Layer is its sophisticated trigger system. This system allows developers to specify precisely when their assertion code should run, creating efficient, targeted security checks.
Trigger types include:
Call Triggers
Execute your assertion when specific contract calls are made:
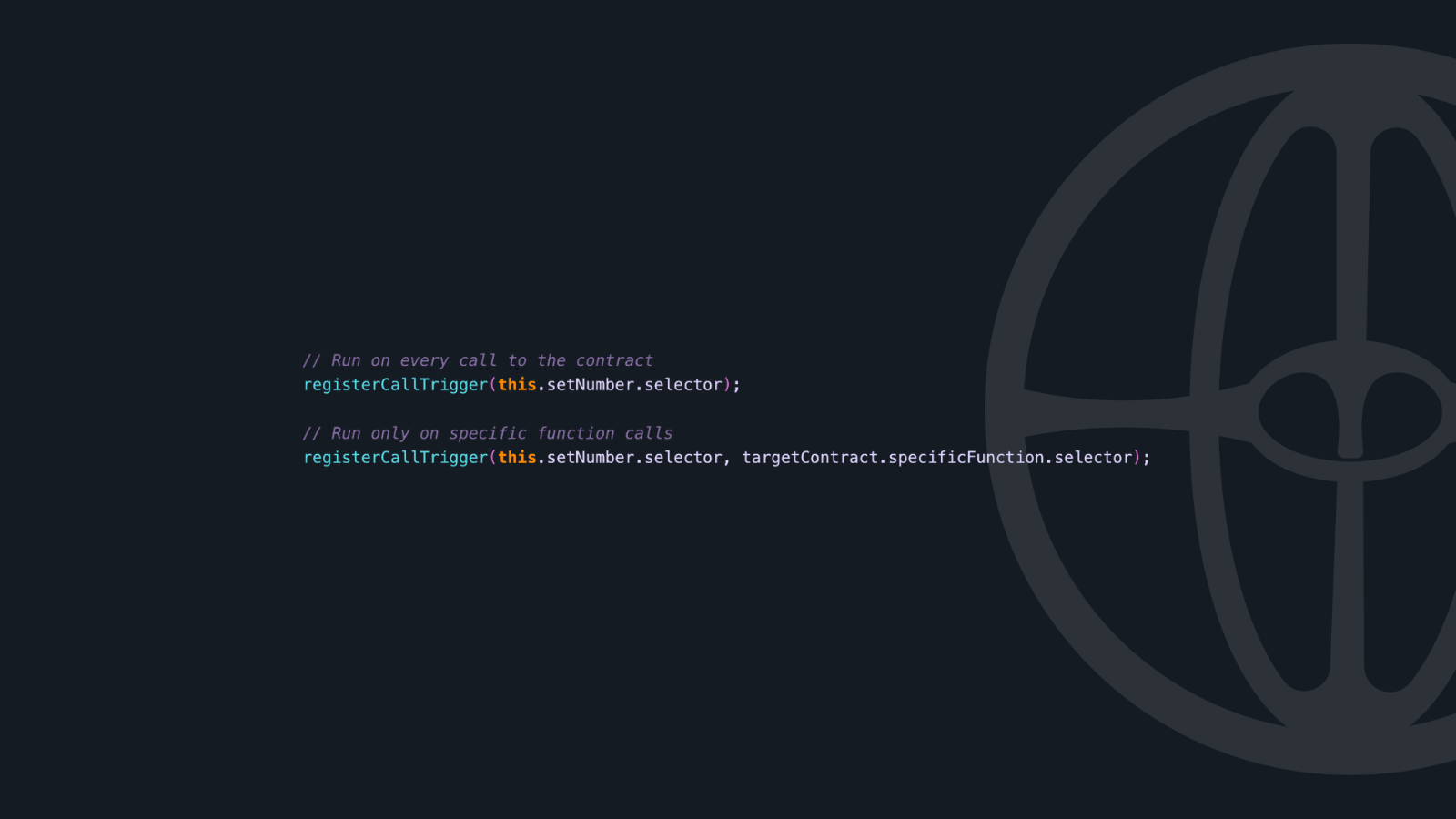
Storage Triggers
Execute when state variables change:
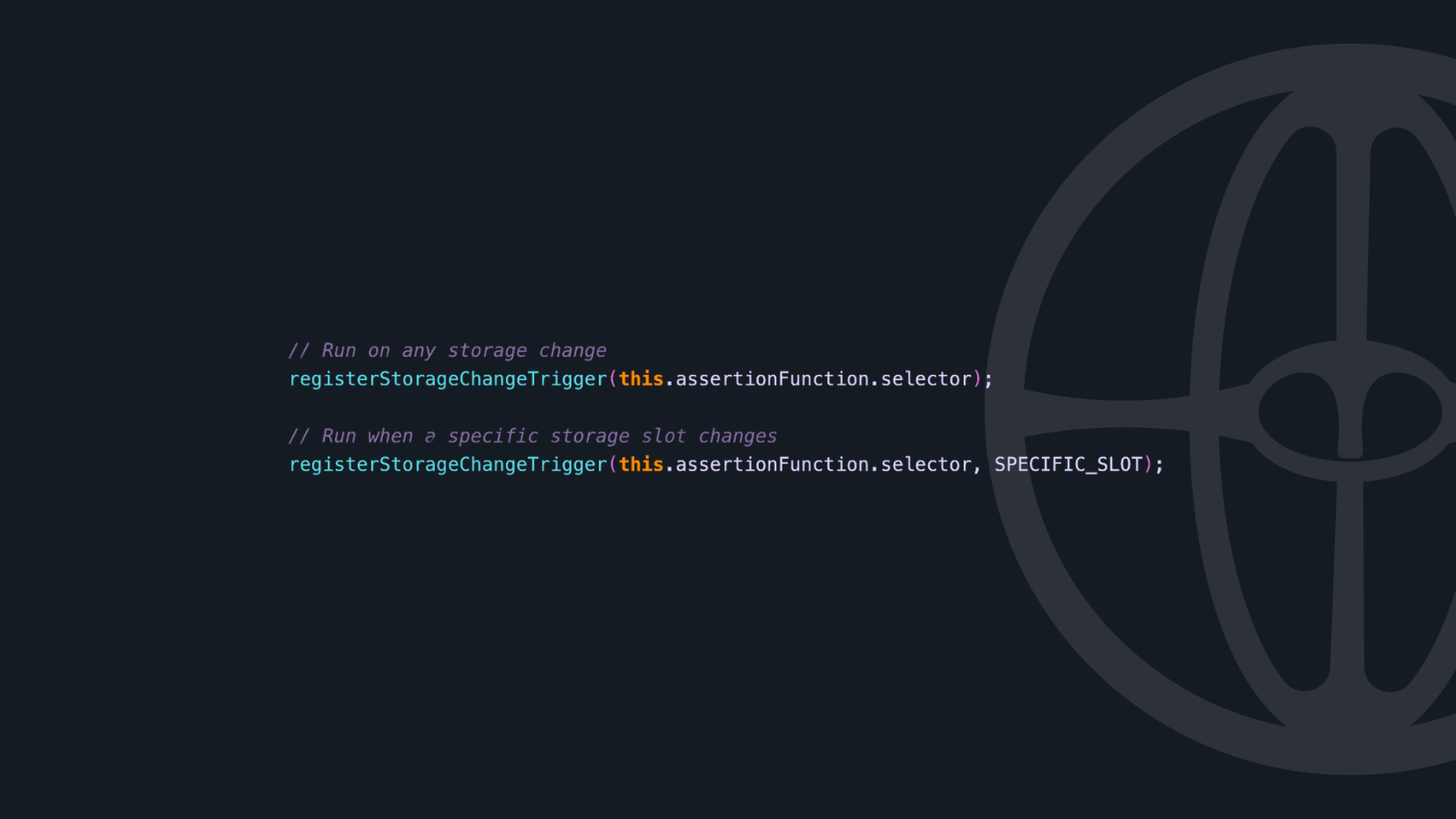
Balance Triggers
Execute when ETH balances change:
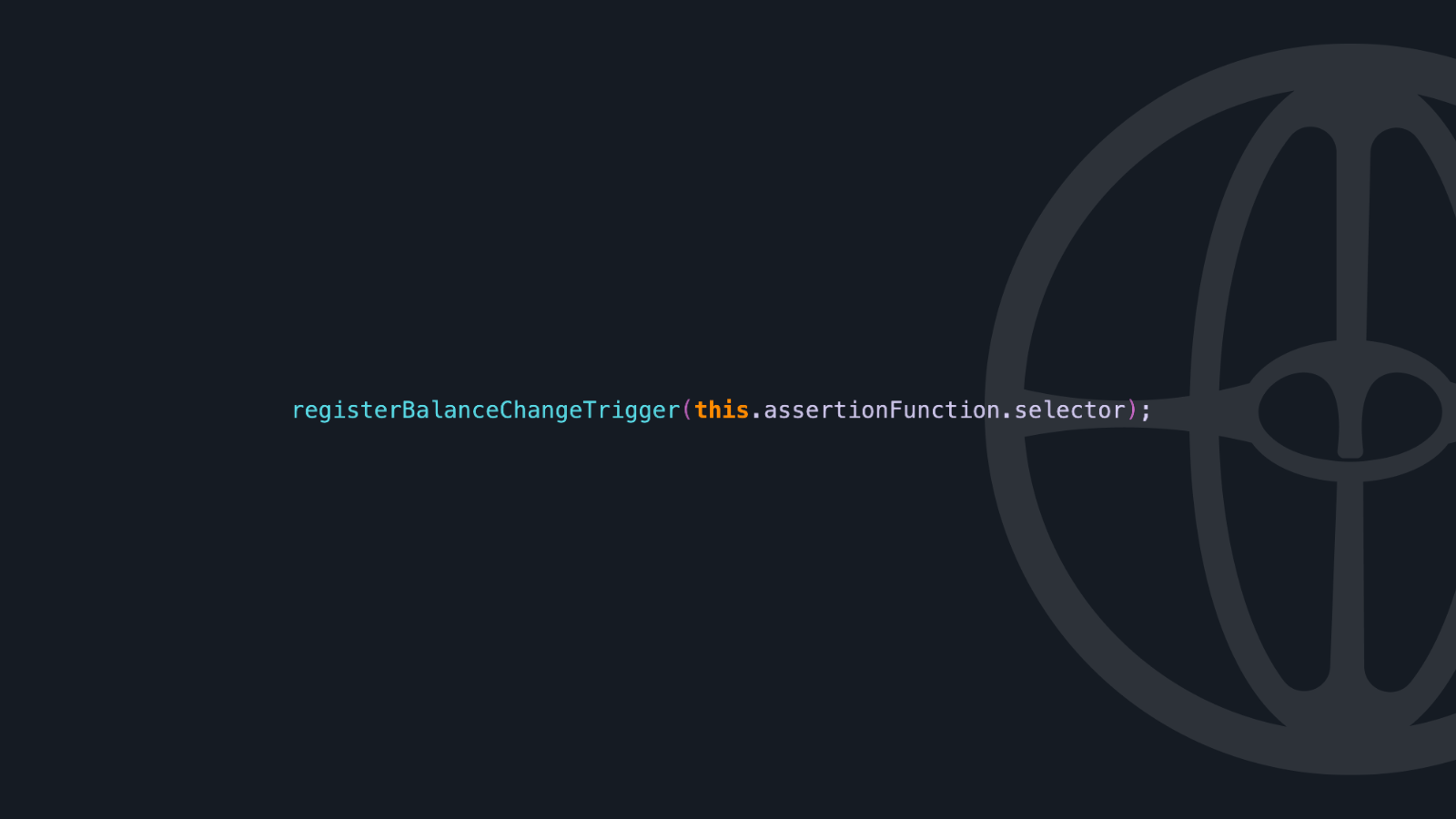
This trigger system ensures assertions run only when relevant, making them both efficient and effective.
What Else Cheatcodes Unlock
Let's explore some of the most powerful capabilities that cheatcodes enable beyond what's possible in normal on-chain Solidity.
Call Stack Inspection
A significant limitation of standard Solidity is the inability to inspect the full transaction call stack. With Phylax cheatcodes, we can examine every call made within a transaction:
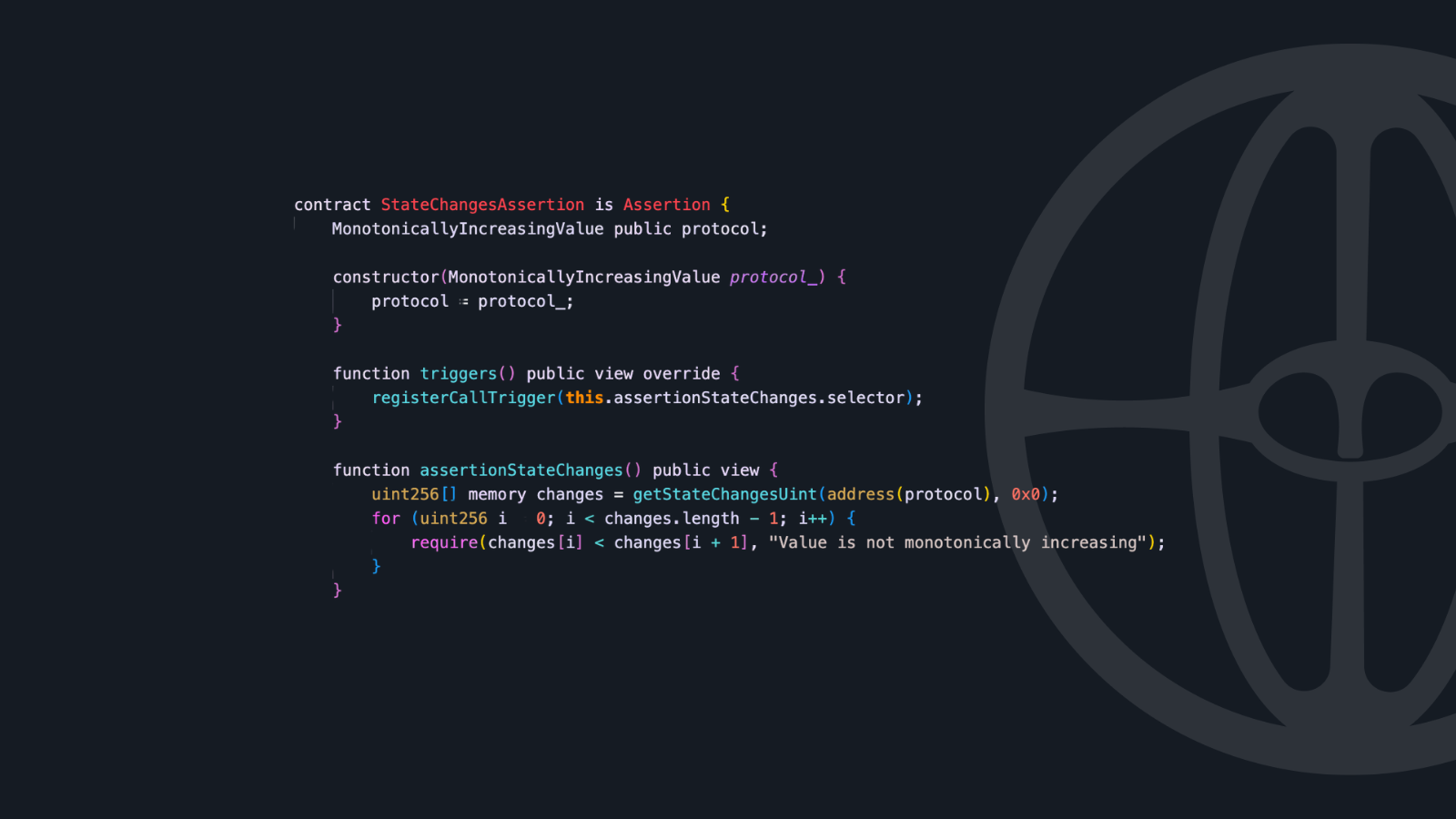
This capability is optimal for preventing unauthorized operations or potential manipulations within complex transactions. An example of this is changing intra-transaction ownership to drain a protocol or similar and then changing it back to the original owner at the end of the call stack as if nothing happened.
Pre/Post-State Inspection
Another game-changing capability is the ability to examine the contract state before and after a transaction:
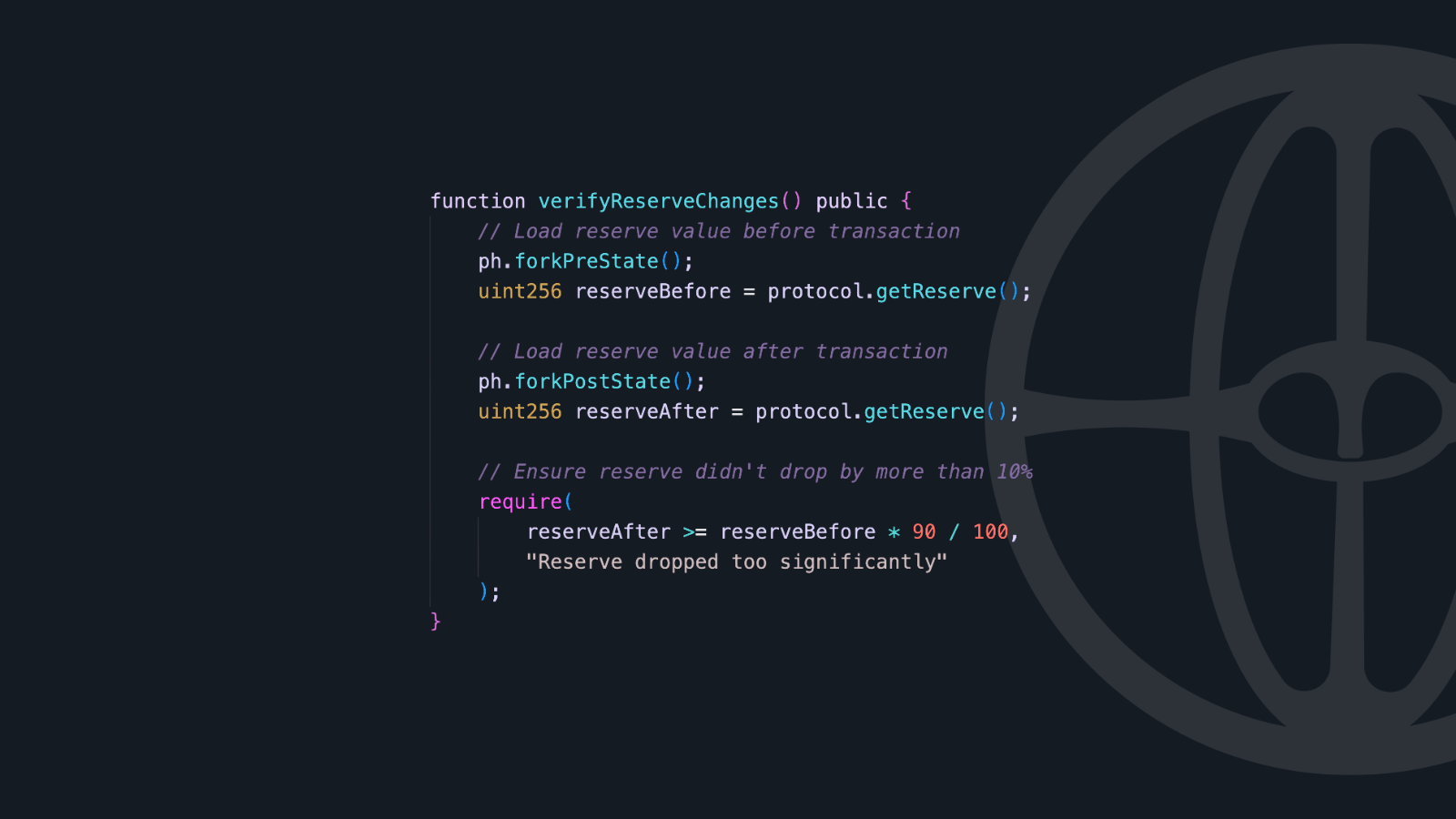
This simple yet powerful pattern enables assertions that compare states across transaction boundaries, which is impossible in standard Solidity.
Storage Variable Tracking
Perhaps one of the most powerful features is the ability to track all intermediate values of a storage variable:
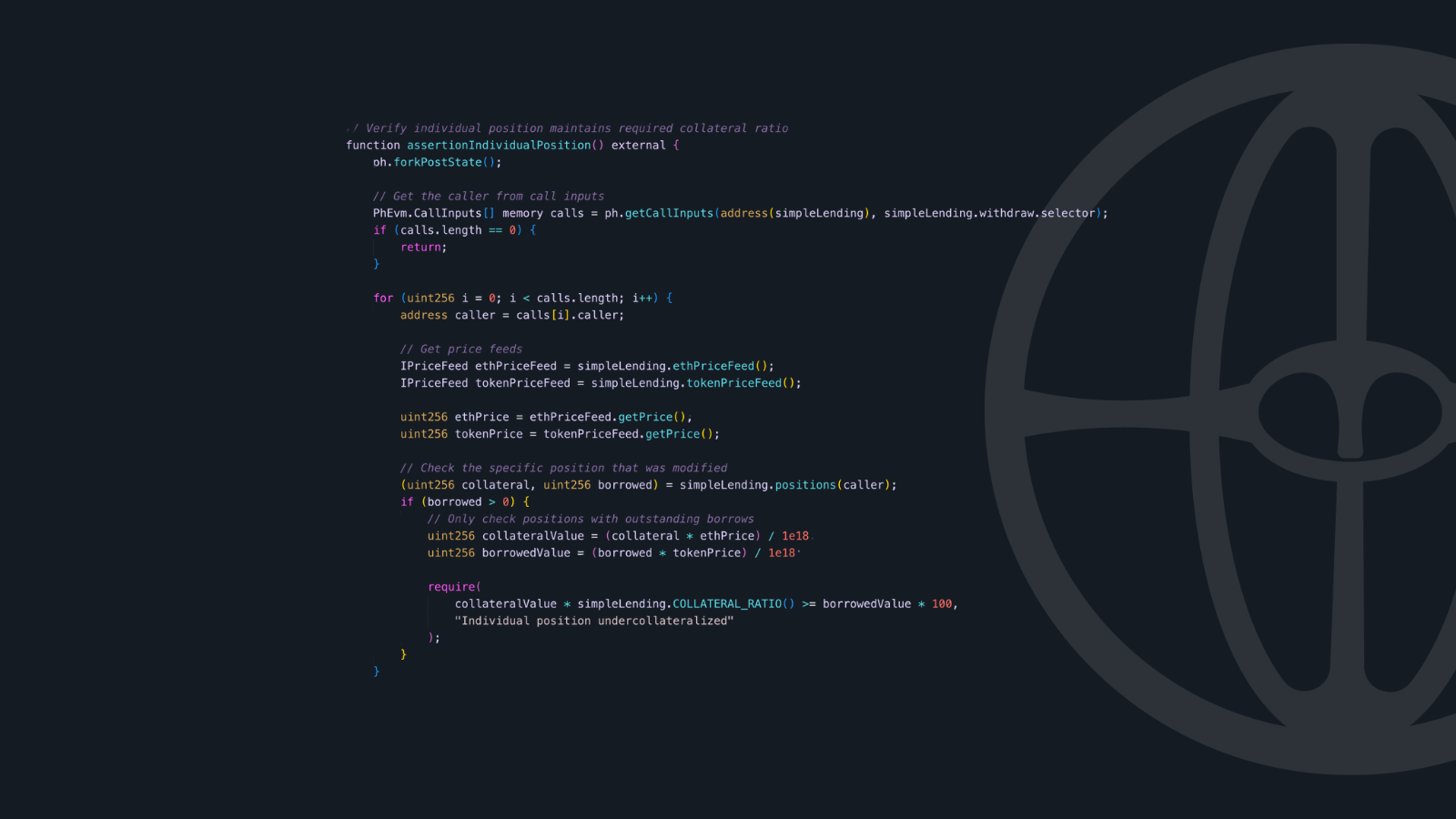
This enables fine-grained assertions about how state evolves during a transaction, catching potentially malicious intermediate states that would be invisible at the beginning of end of a transaction boundaries.
Log Analysis
Logs are a critical part of Ethereum's observability model, and Phylax provides first-class access to them:
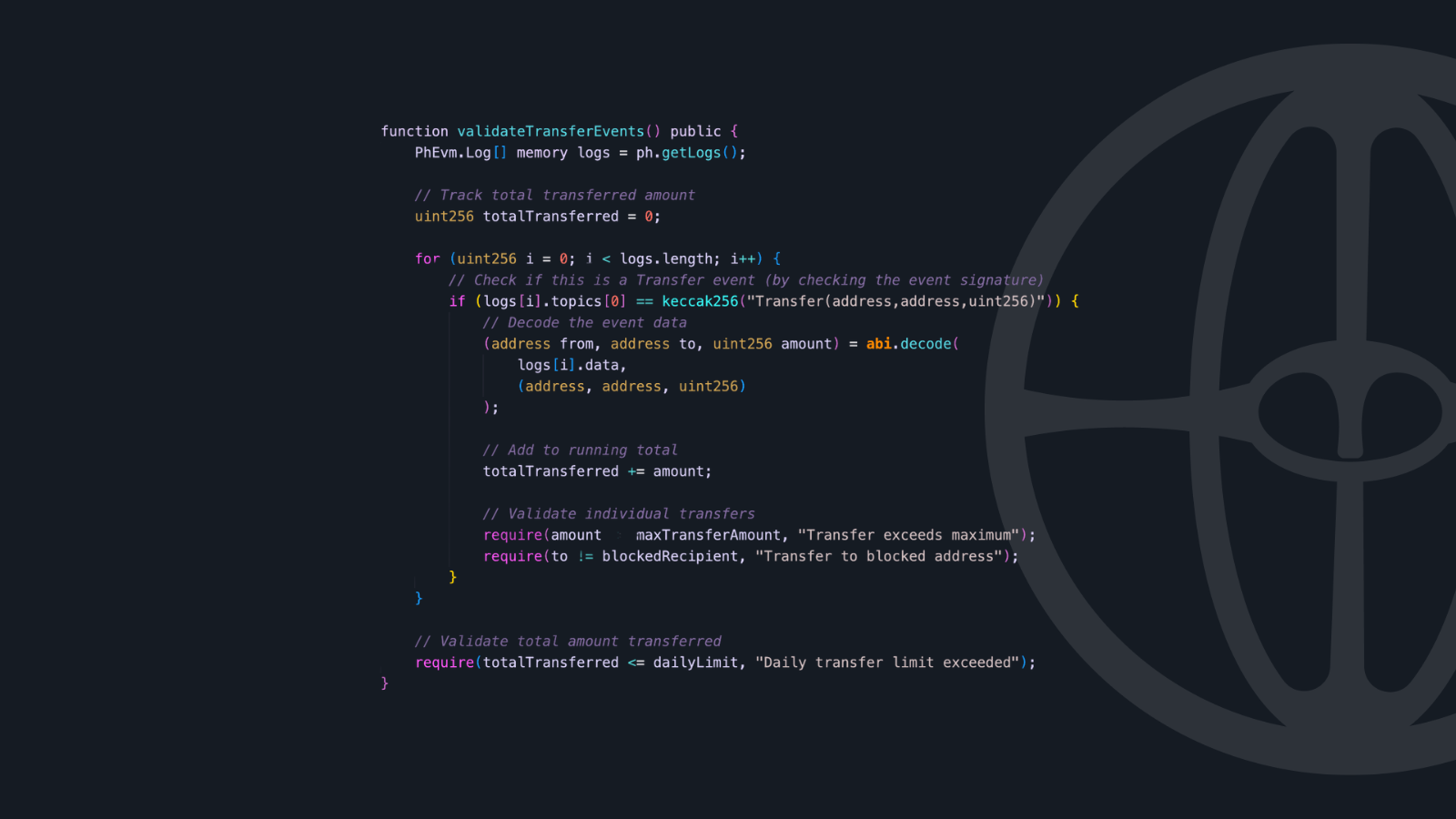
Advantages Over Traditional Solutions
On-Chain vs. Off-Chain Monitoring
Traditional security approaches often rely on off-chain monitoring, which has several disadvantages:
- Delayed response time (can only react after an exploit)
- Reliance on external infrastructure that can fail
- Inability to automatically prevent exploits
In contrast, Phylax cheatcodes:
- Execute synchronously with the transaction
- Can prevent exploits before they complete
- Operate directly within the transaction execution context, providing real-time protection
- Can access and validate state that would be inaccessible to traditional smart contracts
Performance Benefits
Despite their power, Phylax cheatcodes are efficient:
- Execute only when triggered by relevant activity
- Operate at the EVM level rather than as user-level contracts
- Provide optimized implementations of complex inspection logic
- Add minimal overhead to transaction processing
The Simplicity of Using Cheatcodes
Even if they sound complex, Phylax cheatcodes are simple to use. The interface is clean and intuitive, following familiar Solidity patterns without requiring any context switching for Solidity developers. All the cheatcodes follow Solidity's syntax and semantics, allowing developers to stay within the mental model they're already familiar with.
Here's how you might set up a basic assertion contract:
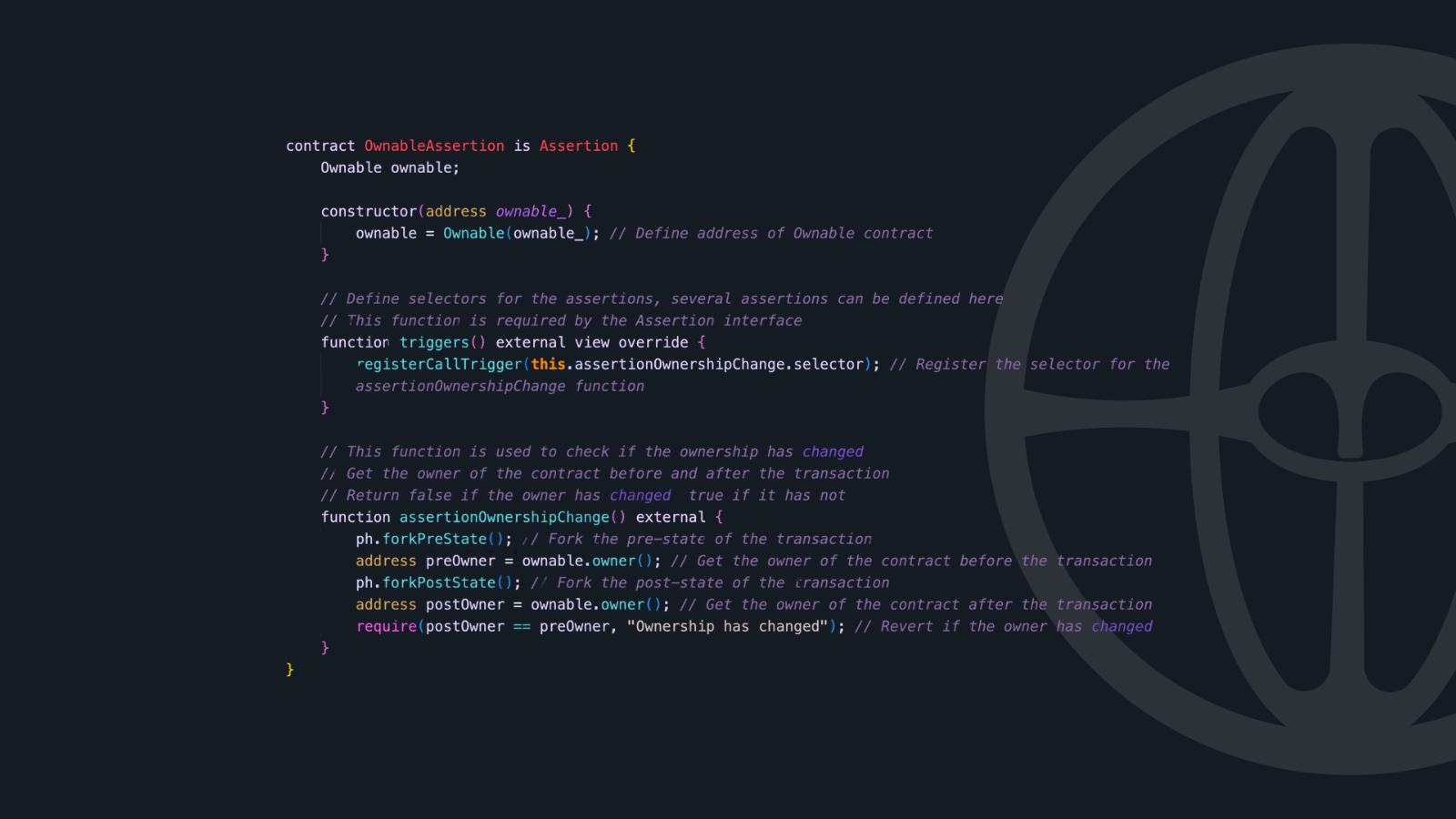
The trigger system makes it easy to specify exactly when your assertions should run, whether that's on specific function calls, storage changes, or ETH balance changes. If you can write Solidity code, you can write Phylax assertions with minimal additional learning.
Easy Testing
Another great feature of the Phylax Credible Layer is the ease of testing assertion contracts. The CredibleTest library and cheatcodes allow developers to simulate transactions and verify assertion behavior before deployment. This is very similar to writing tests in Forge already and all the cheatcodes you’re already familiar with are available:
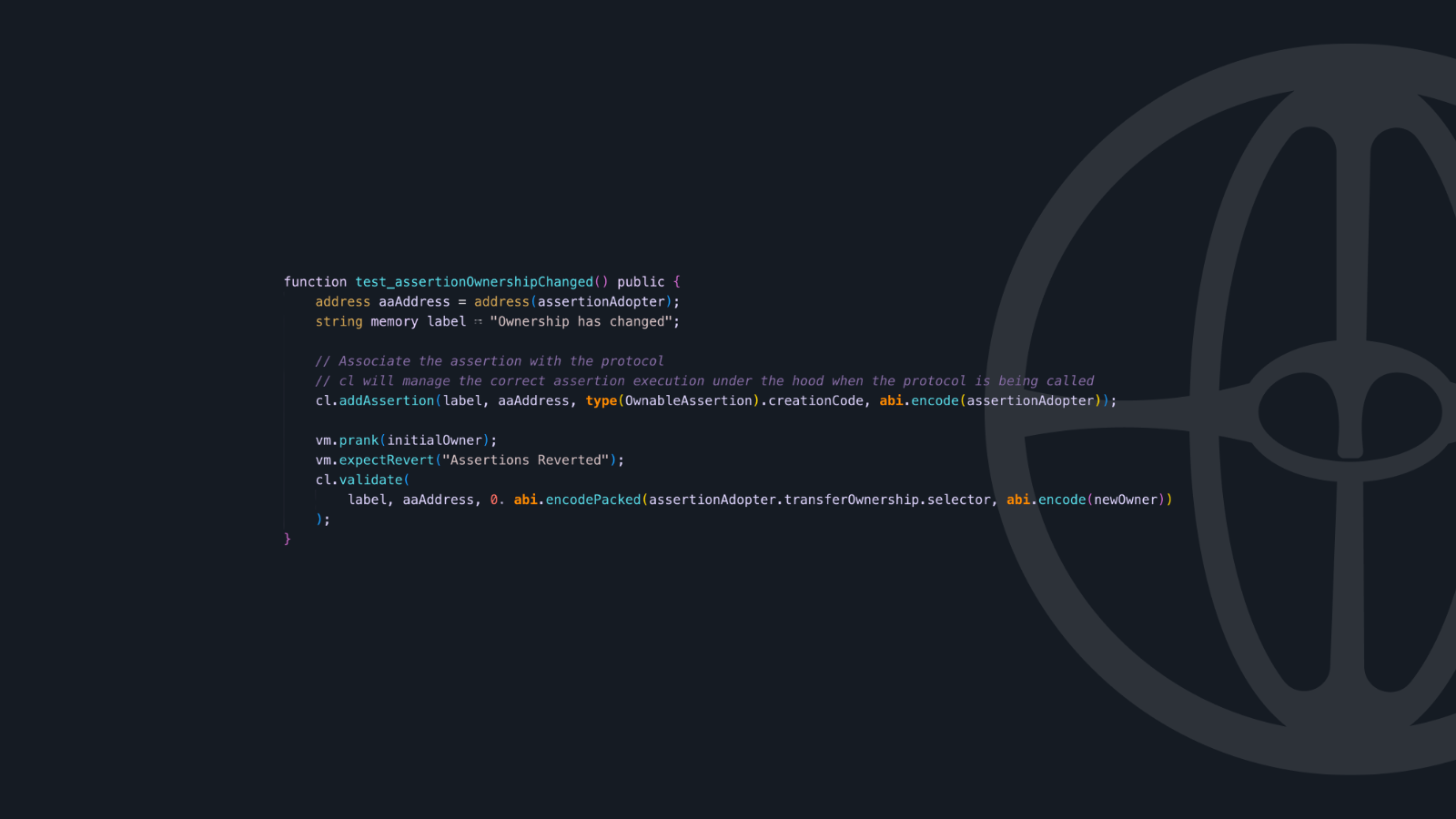
This testing capability ensures that assertions work as expected before they're deployed to protect live contracts.
Conclusion
The Phylax Credible Layer's cheatcodes represent a significant advancement in on-chain security and prevention. By breaking free of traditional EVM constraints, they enable a new generation of sophisticated assertion contracts that can:
- Inspect the entire call stack of transactions
- Compare pre/post-transaction states
- Track all intermediate state changes
- Analyze log emissions in detail
- Enforce complex invariants across function calls
All of this is provided through a simple, intuitive interface that's easy to use and test. As DeFi and other on-chain systems grow increasingly complex, tools like Phylax's cheatcodes will be essential for maintaining security and integrity. They offer a glimpse into the future of on-chain prevention, where sophisticated assertions can catch potential exploits before they cause damage.
The most powerful aspect may be how these capabilities require minimal changes to existing contracts. Assertions using Phylax cheatcodes can be implemented alongside any protocol, providing an additional layer of security without modifying the core contract logic. This separation of concerns allows security experts to build robust preventative solutions without interfering with protocol development.
As the ecosystem continues to evolve, we can expect even more powerful cheatcodes and assertions to emerge, further strengthening the security of the blockchain ecosystem.

.png)
.png)