Intro
In the race for market dominance, technology companies traditionally focus on building moats through distribution advantages, network effects, product superiority, or brand value. Tried and true methods to be sure, yet as these conventional moats become increasingly assailable in our digital age, a different kind of competitive advantage has emerged: security. You might be thinking: "of course a security company would say security is the moat," but hear me out.
While other competitive advantages can be replicated or disrupted, security becomes stronger over time, compounds with trust, and proves nearly impossible to reproduce quickly. In essence, security as a moat is trust built through care and diligence.
That’s why we are building the Credible Layer, to help security towards mainstream adoption through creating a protocol that dApps can use to prevent hacks and users can leverage to verify that their funds are in fact secure.
The age of "trust me bro" security is over. The time for verification has come.
The Erosion of Traditional Moats
Traditional competitive advantages are showing cracks in their foundations and everyone knows it. Here’s how:
Network effects, the darling of Web2 platforms, can be replicated or bridged through interoperability protocols and aggregators. Product superiority is increasingly temporary in an age of rapid innovation and open-source development, where features can be copied within months. Even strong brands, built over decades, can be challenged by well-funded competitors with compelling narratives and modern marketing approaches. Even distribution, the most popular currently faces headwinds from the increasing simplicity of user-generated content that dilutes the popular mind. Additionally, generative AI has changed the content output needed to capture the same attention by an order of magnitude.
More importantly, these traditional moats often work against each other in the modern economy. Pursuing network effects might require compromising product quality. Maintaining distribution advantages might mean sacrificing brand value. The trade-offs between these conventional moats create vulnerabilities that competitors can exploit. But a focus on security offers a unique opportunity to differentiate, with no collateral damage.
Security: A Time-Tested Advantage
Unlike conventional moats, security as a moat, both as a core design principle and the north star when it comes to messaging demonstrates unique characteristics that make it particularly powerful. It should be noted, that what is not meant here is paying lip service to security, but some examples are listed later to make that clear. This advantage manifests in four distinct ways:
- Compound Trust: Each year without security incidents builds consumer confidence exponentially. While a single breach can damage trust, consistent security creates a reputation that becomes part of a company's fundamental value proposition. User trust generated through proven security is the ultimate mechanism for generating stickiness.
- Technical Debt Avoidance: Security-first companies build inherently more robust systems from the ground up. Companies that try to add security later often face insurmountable technical debt and architectural challenges.
- Cultural Integration: Security becomes embedded in organizational DNA, affecting everything from product development to customer service. This cultural element proves particularly difficult for competitors to replicate.
- Asymmetric risk-reward matrix: A hack, whether money or personal data has such outsized consequences for a business that not paying the money and time upfront to avoid this possibility is simply a misunderstanding of risk. Not finding PMF doesn’t kill your business in one day, and neither does not find the right distribution channels.
Consider Apple's approach to privacy and security. While competitors can match their hardware quality, Apple's years of security-first development and privacy-centric features have created a level of customer trust that can't be bought or quickly built. This trust translates directly into customer loyalty and premium pricing power that extends beyond mere brand value.
Here is another example to consider: Microsoft's Trustworthy Computing Initiative represents perhaps the most dramatic example of security transformation creating lasting competitive advantage. In 2002, facing mounting security challenges, Microsoft took the unprecedented step of halting development across its Windows division to focus on security. This decision, estimated to cost over $100 million initially, seemed radical at the time.
The initiative fundamentally changed how Microsoft approached software development. Security reviews became mandatory, development processes were overhauled, and the entire company culture shifted toward a security-first mindset. While this temporarily slowed product development, it created a foundation of trust that would prove invaluable in the cloud computing era.
The media and public responded amazingly. Security is not only good marketing but fundamental to building products that will be used by hundreds of millions of people.
Today, Microsoft's emphasis on security has become one of its strongest competitive advantages, particularly in enterprise computing. While competitors can match feature sets or price points, they struggle to replicate the deep integration of security at every level of Microsoft's ecosystem.
PayPal's story demonstrates how security innovation can become the core of a company's competitive advantage. In its early days, PayPal faced fraud rates of over 1000% - a level that threatened to bankrupt the company. Instead of accepting these losses as a cost of doing business, PayPal transformed fraud prevention into its defining feature.
The company developed IGOR, its proprietary fraud detection system, which combined machine learning with human analysis. While competitors focused on transaction speed, PayPal deliberately added friction through security checks. What seemed like a disadvantage became a strength: customers began to associate payment delays with protection. Today, PayPal's loss rate sits at 0.17% - far below industry averages (more than 1%), representing billions in saved revenue.
Another great example of putting security first and winning big is Cloudflare which entered a crowded CDN market but differentiated itself by focusing on security first and speed second. While competitors promoted faster content delivery, Cloudflare built its reputation on DDoS protection and threat mitigation. This security-first approach transformed Cloudflare from a CDN provider into a critical infrastructure company.
The company's ability to protect against massive DDoS attacks created a network effect: each attack made their protection stronger, as their systems learned and adapted. This security moat proved more valuable than pure performance advantages, leading to Cloudflare's dominant position in web infrastructure.
Google's decision to make HTTPS a ranking signal in 2014 exemplifies how security leadership can reshape entire industries. By prioritizing encrypted connections in search results, Google turned security from a nice-to-have into a business necessity. The company sacrificed short-term search relevance for long-term web security, betting that secure sites would ultimately provide better user experiences.
This move, combined with Gmail's end-to-end encryption and Chrome's security features, positioned Google as a security leader. The company's willingness to enforce security standards, even at the cost of compatibility, has created a lasting competitive advantage in user trust.
Tesla's approach to vehicle cybersecurity demonstrates how security can become a differentiator in traditionally hardware-focused industries. While other automakers treated software security as an afterthought, Tesla built its vehicles with security as a core feature. Their over-the-air update capability, initially seen as a potential security risk, became a security advantage, allowing rapid response to threats.
The company's bug bounty program and proactive security measures have helped maintain trust in an era of increasing vehicle connectivity. As traditional automakers struggle with cybersecurity incidents, Tesla's security-first approach has become a key factor in maintaining its premium market position.
All of these case studies highlight how the largest companies of the last technology cycle leaned into security-focused designs to capture their markets.
And it worked, every single time.
Security: Crypto’s Missing Bridge to Mainstream Adoption
While the crypto industry races to solve scalability and user experience challenges, a more fundamental barrier to mainstream adoption persists in security. The industry's obsession with transactions per second (TPS) overlooks a hard truth – speed becomes meaningless when users fear losing their assets to hacks.
The crypto sector's security challenges illuminate a broader truth about technological adoption: users prioritize safety over speed. Traditional finance didn't achieve mass adoption because it was the fastest – it succeeded because it was the most trusted. Each major blockchain security incident doesn't just affect individual users; it erodes confidence in the entire ecosystem.
For institutions
Institutional adoption of blockchain technology has been primarily hindered not by performance limitations but by security concerns. It is really as simple as the risk curve for crypto is not aligned with institutional investors' risk tolerance. Yes, they are allocating to BTC ETFs and other such investment vehicles but that is hardly “crypto.” While blockchain networks race to implement the latest scaling solutions, institutional investors continue to cite security as their primary concern. The lesson is clear: without robust security, other technological advantages become irrelevant.
“Investors revealed security and safety, ease of use, and regulatory status as the most important characteristics when choosing a digital asset custodian.”
-- Fidelity Digital Assets Report
Security is THE Fundamental Moat
The evidence across both traditional technologies provides a clear indicator to the blockchain sector on how to proceed toward mainstream adoption: security has emerged as the most fundamental and durable form of competitive advantage. Unlike other moats that can be replicated or disrupted, security builds compound advantages that strengthen over time.
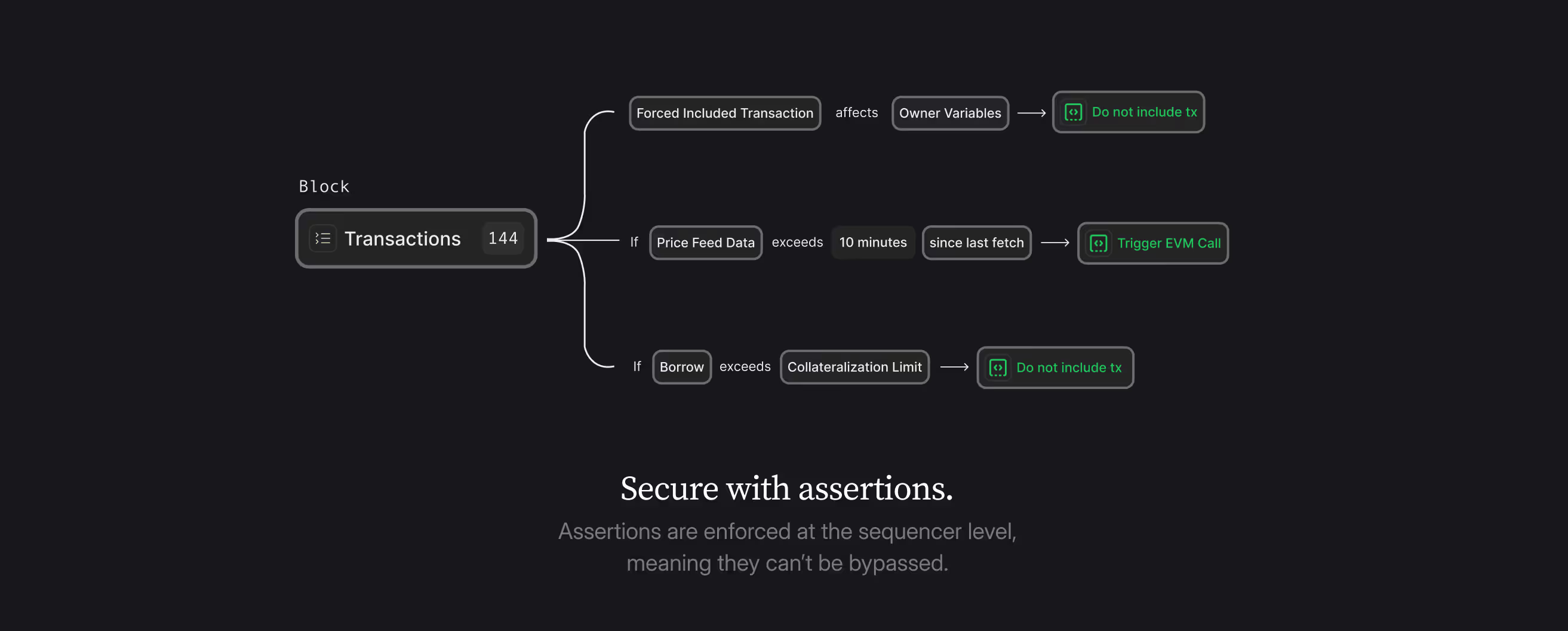
That’s why we are building the Credible Layer, a modular, embedded and verifiable security protocol that makes security for your dApp easy and painless. Our off-chain architecture is non-invasive and unconstrained, making it easy to define what a hack looks like and ensure that block builders and sequencers don’t include transactions that would result in a “hacked” state. We are onboarding the first wave of dApps.
Ask us if we will be deploying to your network(s) soon.

.png)
.png)