In the fast-paced world of crypto, where billions of dollars flow through decentralized systems daily, security is everything. Yet, traditional blockchain security approaches often fall short—they’re reactive, patching vulnerabilities only after they’re exploited.
That’s why we built the PhEVM, designed to enable verifiable, embedded security integrated directly into the block-building process. With a tested capacity of 30,000 TPS, the PhEVM is built to handle high volumes of transactions, validating each transaction to ensure it adheres to the defined security rules.
What is the PhEVM?
It is the copy of the pre-state EVM that the Credible Layer is integrated with, enabling block builders to enforce on-chain assertions defined by dApps. These assertions are custom security rules that describe what a hack or invalid state looks like for a specific dApp.
The result: the integrated network blocks hacks before they can land on-chain and impact users or funds.
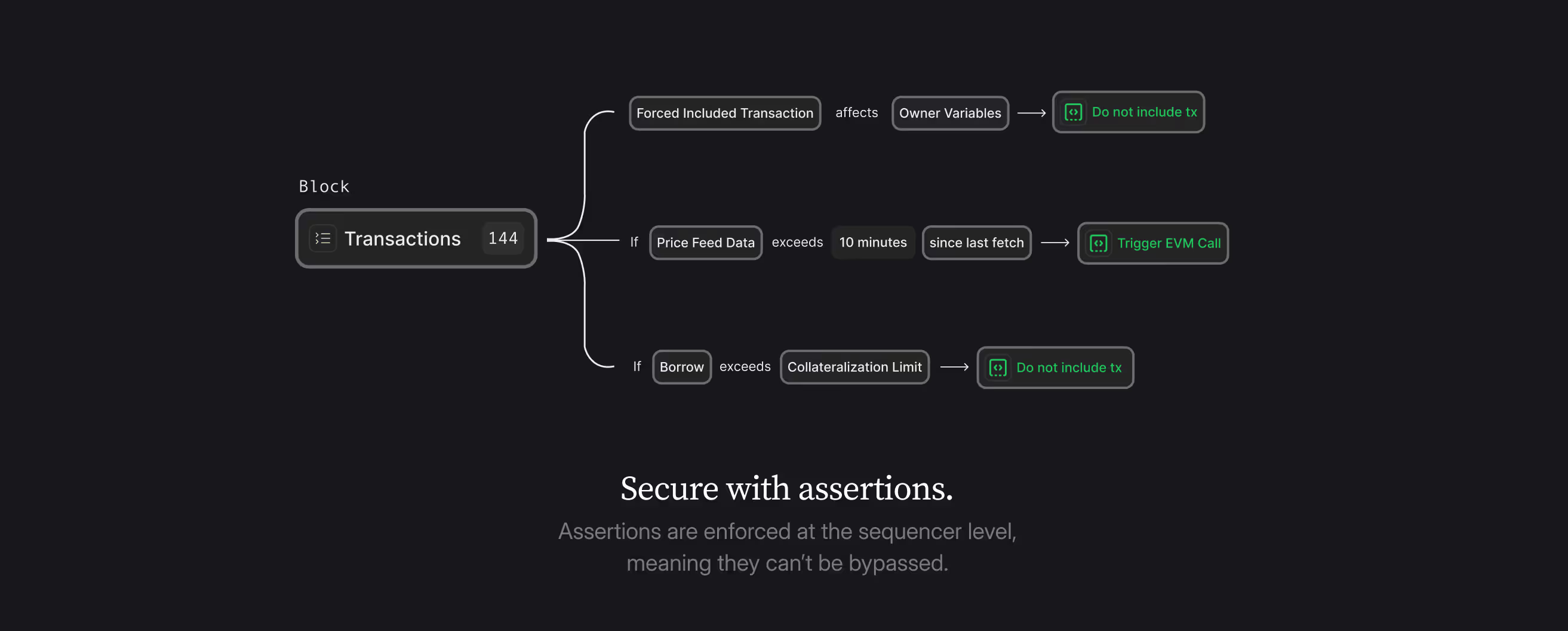
Assertions not only ensure that transactions conform to specified rules, but also provide dApps with the ability to manipulate and compare states. By leveraging the PhEVM, developers can simulate multiple pre- and post-state scenarios, validating invariants across a range of use cases. Whether it’s testing collateralization thresholds, safeguarding liquidity pools, or ensuring accurate cross-chain transfers, assertions empower developers to define and enforce complex rules, enabling a broader design space for innovative applications that extend the scope of dApps.
How Does the PhEVM Work?
- Assertion Writing + Registration: dApps write and register custom assertions on-chain to the contracts they want to protect. These assertions define a specifc state that the transaction should never lead to. Assertions only return binary results: validated/invalidated.
- Pre-Execution Simulation: When a transaction is submitted, the PhEVM runs a pre-execution simulation, evaluating the transaction against all the registered assertions that relate to the contract that the transaction touches.
- Transaction Validation: If the simulation detects that the transaction is invalidated by the assertion, the transaction is rejected before it’s included in a block.
- On-Chain Proofs: Both valid and invalid transactions generate on-chain proofs, ensuring full transparency and accountability for the network’s security guarantees. This means users can finally verify the security measures that each dApp has in place. No more blind trust.
The PhEVM is off-chain?
The PhEVM runs off-chain simulations against the pre-state to ensure that assertions are enforced without introducing a large amount of latency or any overhead to the block-building process. By performing assertion checks off-chain, the PhEVM allows for complex, resource-intensive security rules to be evaluated without slowing down transaction validation.
This architecture ensures that the blockchain remains fast and scalable, while still enabling dApps to define sophisticated, custom rules for what constitutes a hack or exploit.
Additionally, off-chain execution minimizes gas costs and increases the complexity possible in assertions. This means you can write assertions that are larger in size and more complex in the information and functions they hold and operate with. Once assertions are checked, on-chain proofs are generated to provide transparency and verifiability, ensuring users can verify the system’s integrity without sacrificing performance.
Simply put, we are leveraging the verifiable nature of blockchains, and the low latency of off-chain systems to bring the best of both worlds to on-chain security.
Why the PhEVM Matters
The PhEVM represents a paradigm shift in how blockchain security is approached. Instead of trusting that a protocol is safe, users can now verify that protocols enforce their own security policies through publicly accessible, on-chain assertions. This shift from “Don’t Trust, Verify” to “Always Verify” is crucial for crypto’s long-term success and mass adoption.
At Phylax, we believe that better security means transparency, more capital, and ultimately, more users. The PhEVM is the next step in ensuring that decentralized ecosystems remain both secure and scalable.
If you’re building on an OP Stack chain or considering security-first solutions for your protocol, we’d love to chat. Reach out to us here.

.png)
.png)