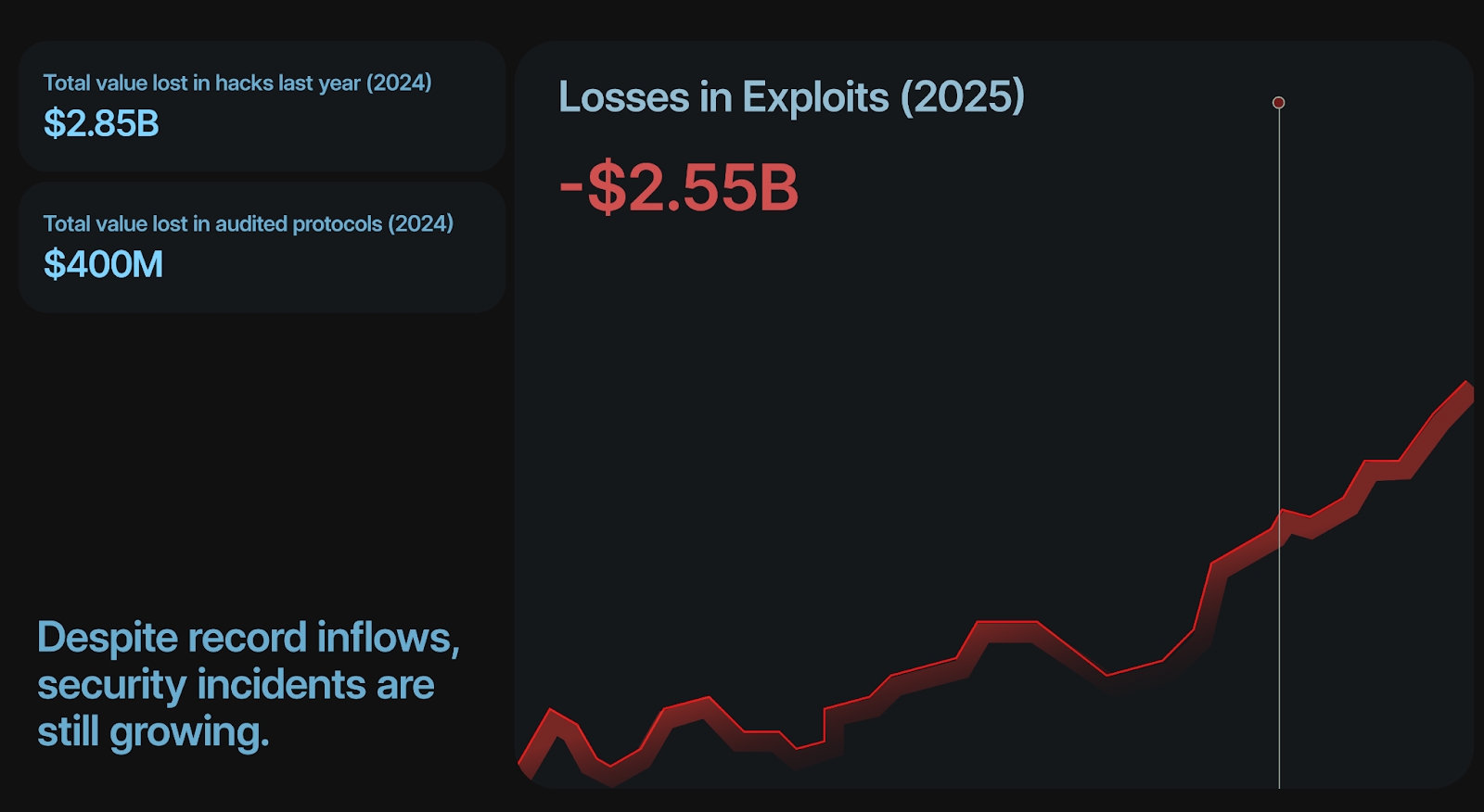
In crypto code is law, but what happens when the code is wrong? What happens when there is a hack?
Smart contracts execute with finality. Once a transaction is finalized, it cannot be reversed, a feature that brings both trust and speed but also risk. While finality ensures transactions can't be tampered with after execution, it also means that when attackers successfully exploit protocols, their transactions are permanent. This means you have to stop a hack before it happens.
Even with audits, monitoring tools, and a range of other security tools, more than $2 billion was stolen in 2025.
Today, we're excited to announce our partnership with Linea to integrate the Credible Layer directly into their infrastructure. This integration brings network-native security to Linea: eliminating the security problem that has kept institutions on the sidelines of DeFi. This is achieved by providing protocols with deterministic certainty that hacks cannot execute, if defined, while maintaining full throughput and composability that make Linea powerful.
"Linea is the first network to activate infrastructure-level exploit prevention as part of the Linea Stack, and we believe this is what will unlock institutional capital for DeFi," said Declan Fox, Head of Linea. "Institutions need deterministic controls built into infrastructure, not monitoring tools that detect problems after they happen. This removes the barrier that's kept billions on the sidelines. But it's not just for institutions, DeFi users providing liquidity or deploying capital want the same assurance that protocols are protected from exploits. Being first to market with this capability, now available to any network using the Linea Stack, positions us as the natural home for both institutional and retail capital."
The Problem with Current Security
Current DeFi security operates on a reactive model:
- Audits are point-in-time and akin to looking for a needle (bugs) in a haystack (code)
- Monitoring tools detect suspicious activity, but often too late to prevent damage
- AI prevention tools require trusting external entities, are prone to false positives, and are somewhat of a black box, making it hard to trust them
Introducing Network-Native Security
Most security solutions sit on top of blockchains as external services, monitoring transactions after they happen and requiring developers to trust third parties to execute mitigations. This introduces new points of failure.
Network-native security is different: it's built directly into the blockchain's infrastructure and inherits the same trust assumptions as the network itself.
The Credible Layer introduces a new security primitive that is a codified protocol invariant: the assertion. Instead of trying to anticipate every possible attack vector, developers define the states that should never occur for their contracts. In other words: hacks. These assertions are then enforced deterministically by the network itself, with every transaction that violates your assertions being removed at the sequencer level. No one except the owner of a contract can write assertions for that contract. This ensures there is no censorship risk.
With the Credible Layer integrated into Linea's sequencer, assertions aren't enforced by an 3rd party that could go offline or be compromised. They're enforced by the same infrastructure that processes your transactions. If you trust Linea, you automatically trust it to enforce your assertions. Your security has the same uptime as the chain.
Here's what makes this different from every other security solution:
- Inescapable, Rule-Based Security: The network removes every transaction that violates your assertions during sequencing. This means there are no false positives, and it is nearly impossible to circumvent due to the level of integration.
- Easy to Use: Written in Solidity, with foundry-like syntax, assertions are faster and more expressive than smart contracts, with no contract modifications or downtime during implementation.
- Verifiable and Transparent: All active assertions are public and verifiable. Users can inspect the exact assertions protecting their funds, and developers can fork proven rule sets from similar protocols.
How It Works for Developers
1. Define Your Assertions
Assertions are functions that map blockchain state to boolean values (hack or not a hack), written in Solidity:
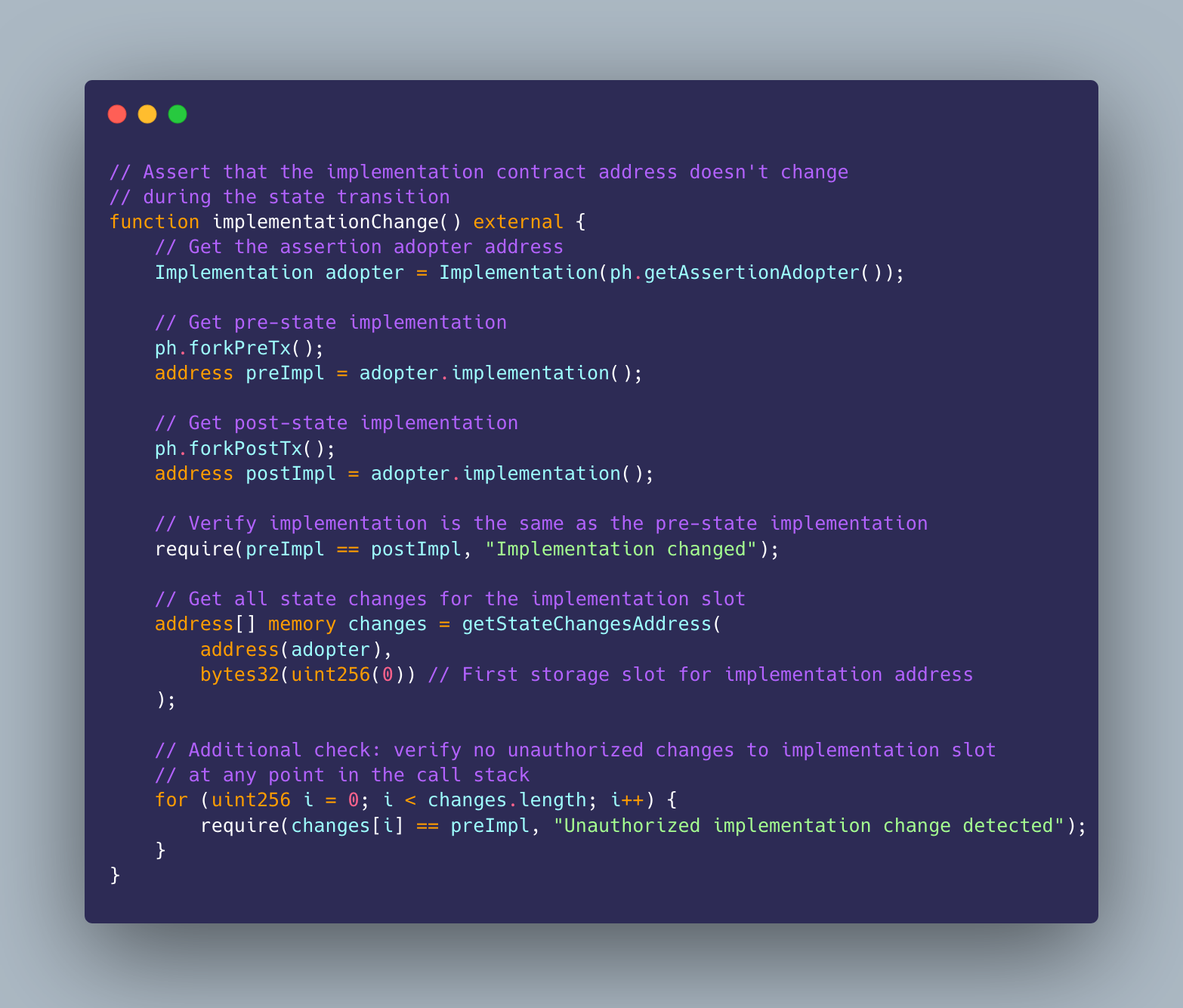
2. Deploy and Register
Deploy your assertions as smart contracts and register them through our app. You can:
- Add new assertions as you discover potential attack vectors or add functionality to your core contracts
- Remove existing assertions or add new versions when necessary
- Fork battletested assertions from similar protocols to bootstrap security quickly
“I use Foundry and Solidity every day. If I don’t have to context switch, that’s much better. If I can also use the existing repositories and test infrastructure, that’s the maximum developer experience. I am thinking about invariants as I create the test suite, so it’s easy to translate them to assertions.”
- Arcadia Finance
3. Network Enforcement
Once registered, Linea's sequencer automatically:
- Simulates every transaction against your assertions before execution
- Drops transactions that violate any active assertions
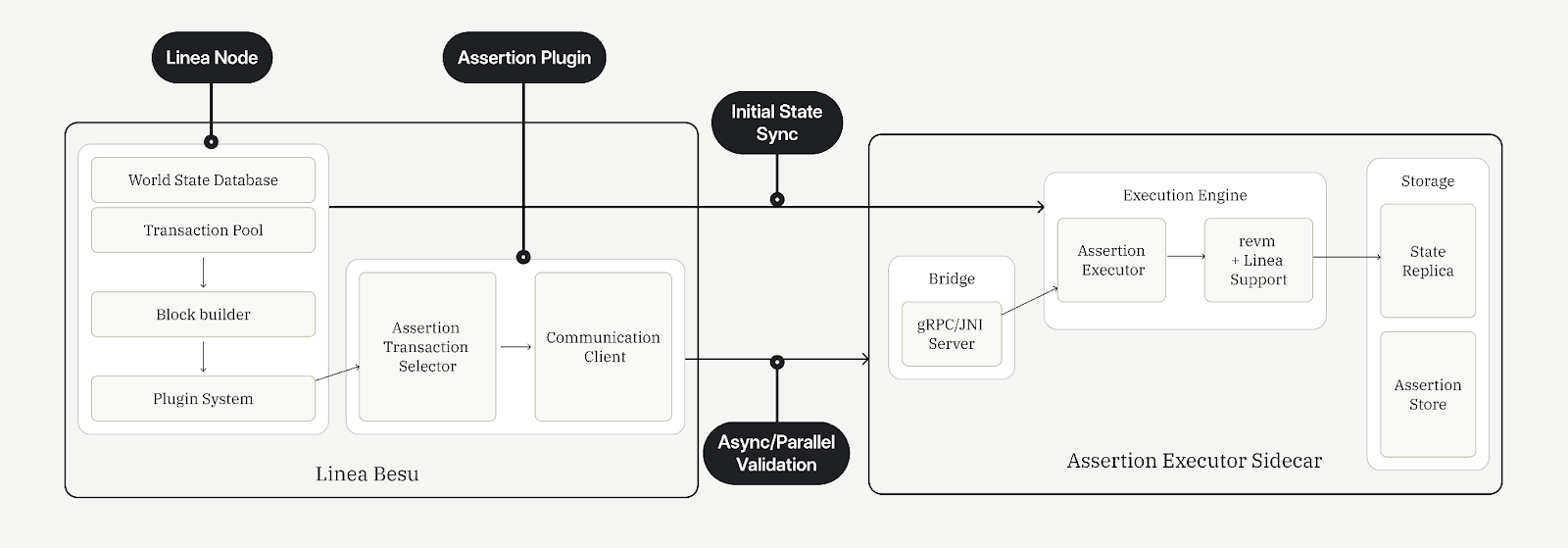
It’s simple for any network to integrate the Credible Layer. Depending upon your architecture, you add the Credible Layer sidecar into your block builder so that when blocks are being built, they are being checked in parallel against active assertions. Notably, this means that your chain stays sovereign and doesn’t rely on Phylax or anyone else for running the Credible Layer, and throughput isn’t throttled because block building and transaction validation via the sidecar happen in parallel. For Linea, this integration meant very few changes to their codebase. If you’re curious how this would work for your chain or block builder, we’d love to hear from you.
4. Transparency and Trust
All assertions are onchain and publicly available. Users can verify exactly what protections are in place, and institutions can assess protocol security programmatically rather than relying on security theater. This is massively helpful as regulations for DeFi participants become clearer.
This transparency solves a critical problem for institutional adoption: how do you evaluate the actual security of a protocol beyond marketing claims and audit PDFs? Assertions are code that anyone can read and verify. Institutions can programmatically assess risk by examining the specific invariants a protocol maintains and is actively enforcing via the network, rather than trusting promises about "robust security measures."
For protocols that use the Credible Layer, this creates a clear security trail. Instead of lengthy due diligence processes trying to understand another protocol's security posture, you can simply review their assertions to understand exactly what states they prevent and how comprehensive their protection is.
"Assertions would significantly reduce the time and resources to assess risk when using or collaborating with other protocols. If the project had assertions, that tells me something about the team's approach to security. I can check if that team had an invariant in place, and how it was defined."
- 0xstorm, ex-Head of Security at Yearn
Real-World Examples
The "Holy Grail" Invariant: Euler Finance
Euler's modular lending architecture lets anyone deploy isolated lending markets, with users borrowing against multiple collateral types across vaults. The core risk: bugs in any vault could cause healthy accounts to become liquidatable without cause.
Their primary assertion, nicknamed "The Holy Grail" based on Certora's early invariant work, enforces: if an account was healthy before a transaction, it must remain healthy after. The assertion monitors all EVC operations, queries accountLiquidity() before and after, and blocks any operation that would make a solvent account vulnerable to liquidation. One assertion protects the entire permissionless vault ecosystem at the network level.
Assertion Versatility
Launch partners demonstrate how assertions adapt to different architectures:
- Euler deployed five assertions to protect various critical aspects of their lending protocol.
- Malda Protocol (cross-chain lending) uses six assertions for account liquidity validation, outflow volume limiting, and rebalancer allowlists.
- Turtle/Lagoon (private credit) protects its dual-mode vault architecture with assertions that enforce mode integrity and settlement ordering.
- Denaria deployed one powerful assertion to protect liquidations in their perpetual protocol.
The integration effort was minimal across all partners. As Malda's team put it: "Do you want to allocate maybe five to ten hours of developer capacity and increase the security of your protocol?"
Lagoon's team found the transition natural since they already write tests in Solidity: "Moving from our test suite to the invariants was quite easy... it gives me the feeling that the test suite we built is run all the time on every operation."
The consistent theme: protocols want prevention, not incident response. Lagoon already uses well-known monitoring solutions, but wanted something stronger: "We would prefer something preventive and not something that is a response to the problem. We don't want it to happen."
We are constantly researching and adding new features in the form of cheatcodes to enable new use cases. Reach out if you want to explore with us.
Why Linea x Credible Layer?
Recently, Linea had Sharplink Gaming (SBET) deploy $170M onto Linea.
Linea wanted to increase the security of the network to shift the risk curve for capital, not partner with another external monitoring service that developers would need to trust and maintain. They understand that institutional adoption requires transparent risk controls that can be verified and audited.
Most importantly, Linea wanted to maintain sovereignty. They needed security that inherits the same trust assumptions as their network without introducing counterparty risk. This is especially important to the dApps and the institutions that allocate to them.
It is also increasingly important to have security, per the recent FTC ruling that requires companies to have circuit breakers and security practices, and decentralized security at that, so that decentralized systems stay decentralized per the Clarity Act.
The developer experience was equally critical. Linea's ecosystem thrives on accessibility, so developers shouldn't need to learn new languages or frameworks just to secure their protocols. With assertions written in familiar Solidity syntax, the integration feels native rather than bolted on.
The result is deep infrastructure integration where every transaction on Linea gets validated against protocol-specific assertions before execution, making preventing hacks more trivial.
The Result
Instead of playing defense against known attack vectors, protocols on Linea can now define their assertions and let the network enforce them deterministically.
For institutions and retail investors evaluating DeFi, assertions provide the transparency and guarantees needed to deploy capital at scale. Unlike AI-powered monitoring systems, which often yield false positives and opaque decisions, assertions provide deterministic certainty that specific states cannot occur.
[insert picture of one of the projects that we are launching within the transparency dashboard]
For developers, it's a powerful new primitive that makes protocols more robust without sacrificing composability or requiring complex integrations. Being able to deploy assertions quickly and at little cost means you can go to market fast and cheaply while proactively reducing the chances of a hack, making it easier to attract capital with more conservative risk profiles.
Getting Started
Developers can leverage network-native security easily:
- Identifying Protocol Invariants: What states should your protocol never enter?
- Writing Assertions: Define the Solidity functions that check these conditions
- Testing Scenarios: Write tests for these assertions
- Planning Integration: Deploy the assertions to Linea
Go to the Phylax Docs to start: https://docs.phylax.systems/credible/credible-introduction

